Internal threats are a critical concern within organizations, with departing employees representing a potential source of significant cybersecurity risk. Whether unintentionally or intentionally, employees can become major insider threat to the security of an organization.
IT leaders are particularly wary of this, as 90-95% of them identify the workforce as the top insider threat. Given the internal access employees have to the organization’s systems and data, they hold the potential to execute devastating cyberattacks from within (Insider Risk Management).
Additionally, internal threats are magnified as certain employees hold access to profoundly sensitive and confidential data, positioning them as potential conduits for data breaches. Unveiled by a Varonis report, this distressing revelation highlighted that a majority of the surveyed companies permitted unrestricted access to over 1,000 sensitive files for every employee. This unsettling figure underscores the internal vulnerability of the entire organization to focused attacks, specifically designed to capitalize on the easily accessible trove of sensitive data.

Internal Threats
When it comes to internal threats, malicious insiders pose a dangerous risk. These actors willingly seek damage to the organization and have internal knowledge and privileges that can be capitalized on in an attack. This seriously harms their target. You might have a internal malicious actor sitting right next to you… Plotting their attack as you read this. They might even be thinking about using you as a pawn. The seemingly innocent look on their face is nothing but a façade.
Only 5% of internal cyber incidents were carried out by employees with malicious intent. So, although you can probably rule out your colleague, you should remain vigilant. Anyone could be a insider threat.
A more common scenario is when an employee, acting with negligence or carelessness, accidentally triggers a cyber breach, highlighting the significance of addressing internal threats (Human Factors in Cybersecurity). Similarly, staff members that are unaware of cyber risks, and the various social engineering techniques used by bad actors, can be an insider threat. Careless and uninformed staff cause a worrying 23% of cyberattacks. You should now be looking at all colleagues surrounding you, including yourself.
The mouse that you used to click on this very article could be concealing a Rogue hardware device (MouseJack Attack) that has the potential to inject keystrokes and cause data theft, malware injection, and more.
There are several causes for internal attacks, but some of the most prominent are:
Malicious:
- Disgruntled employee.
- Activist against the organization’s agenda.
- Mole.
Careless or uninformed:
- Lack of education or training.
- Complicated rules and regulations that are too difficult to understand.
- Poor cyber hygiene.
Devices Are an Asset and a Liability
Organizations have, for some time now, been equipping their staff with company-owned devices intended for remote work. Whether these devices are permitted for personal use depends on the organization’s cybersecurity department and relevant policies. Though such practices can introduce heightened security challenges related to internal threats.
Depending on the organization’s work from home policy, these devices typically provide users with remote access to the organization’s network and confidential information. Moreover, sometimes even storing such information on the endpoint itself. Great, right? Well, yes, thanks to these devices, many organizations were able to continue some, if not all, operations during the most disruptive period in recent history.
Unfortunately, that is about as positive as this blog is going to get. Endpoints are susceptible to hardware attacks whereby a spoofed peripheral – which is by design, malicious – is connected via the USB interface. Since these Rogue Devices impersonate legitimate HIDs, no security alarms are triggered. And the peripheral, or rather the attacker, has access to the unsuspecting (Bad USB) user’s device. From here, depending on what the endpoint provides the user with access to, the attacker can commit data theft, inject malware, carry out espionage activities, and initiate a ransomware attack, to name a few.
Internal Threats Posed by Employees and Remote Devices
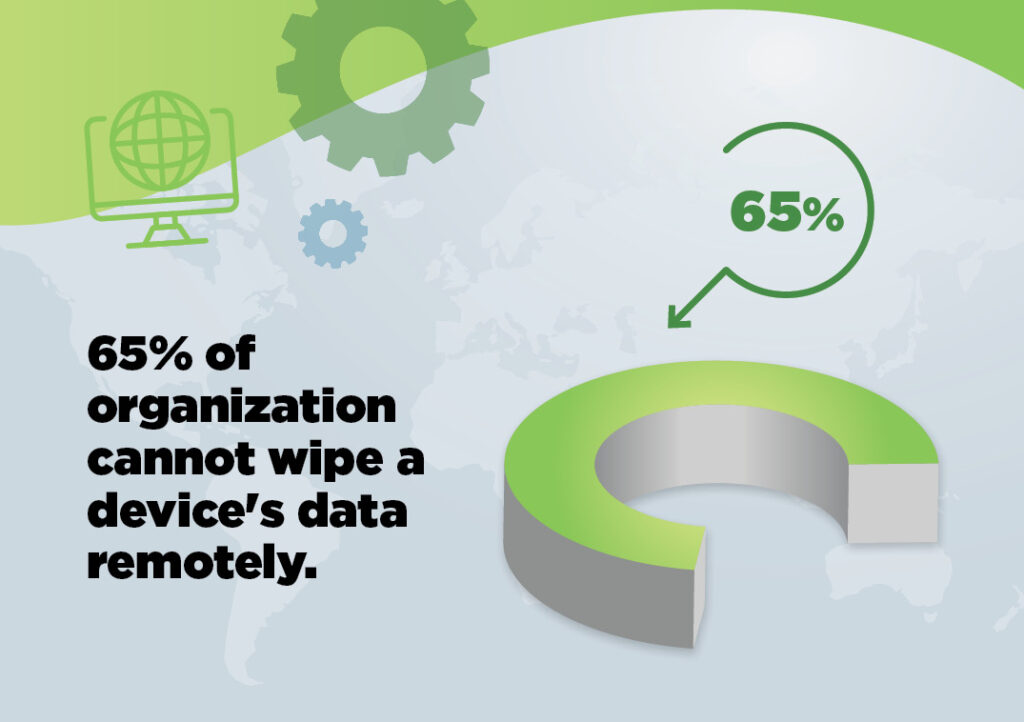
The risks associated with employees internal threats and remote devices are always apparent. Organizations need to be on constant alert for attacks originating from both sources. However, when the two are combined, the threat is even more significant. Let me explain… What happens when an employee is terminated? You cut off that employee’s remote access privileges, obviously. Okay, but what about the data stored on the device? Shockingly, 65% of organizations cannot wipe devices remotely. Therefore, the terminated employee still has access to such data until they are no longer in possession of the device. An exemplar of the numerous internal threats that organizations must contend with.
This is where the risk comes in. You now have an individual who has just lost their job, has nothing to lose (relatively speaking), and has access to sensitive data belonging to the very organization that put them in their unenvious position. A hardware attack is looking pretty appealing. This is especially because the tools are relatively cheap, go undetected, and can cause significant damage to the victim. Now that is a disgruntled employee if there ever was one.
But that is not the only risk. Yes, there are more. A laid-off employee may not wish to cause harm to their ex-employer, but their carelessness could be just as damaging. A lack of cybersecurity awareness could result in an ex-employee recklessly discarding the device. The inability to wipe the data remotely means that such negligence on the employee’s behalf puts the organization at significant risk. Was the device unknowingly sold on eBay to a dangerous hardware attacker? Was the device handed down to a friend or family member who hastily attached a vulnerable peripheral to it? The possibilities are endless and the list of damage that internal threats can cause goes on…
We are here to help!
Yes, I tricked you when I said there are no more positives to this blog… you are welcome.
Sepio’s platform provides, well, a solution to this problem. HAC-1 Hardware Access Control’s capabilities have resulted in a real-life use case where a client used the software to find a loophole to the issue at hand.
Sepio provides organizations with complete visibility of all hardware assets within their infrastructure, including remote devices. In doing so, Sepio uses Physical Layer fingerprinting technology and Machine Learning to calculate a digital fingerprint from the electrical characteristics of all devices and compares them against known vulnerable and Rogue Devices. Additionally, the solution allows the system administrator to define a strict, (Granular policies), set of rules for the system to enforce.
When a device breaches the pre-set policy, Sepio automatically instigates a mitigation process that instantly blocks unapproved, or Rogue hardware. With these administrative benefits, our client blocked all peripherals by setting the solution in ARM mode for the specific employee’s device considered an insider threat. Doing so rendered the machine useless. So whether they were a malicious actor or just a careless one, there were zero risks of a hardware attack originating from their device.
Just because many organizations struggle with wiping a device’s data remotely, that does not mean that there is not a way around the problem; and Sepio is the secret weapon.
See every known and shadow asset. Prioritize and mitigate risks.
Talk to an expert. It will help you understand how to use Sepio’s patented technology to gain control of your asset risks.

