What is Remote Work Cyber Security?
Remote work cyber security refers to the practices, technologies, and measures used to protect remote work environments from cyber threats. With employees working from various locations and using both company-issued and personal devices, cybersecurity challenges have evolved significantly.
As remote work security becomes a global priority, organizations must address emerging risks. Whether employees use personal (BYOD) or company-provided devices, unsecured connections and non-company peripherals increase the risk of breaches.Given the growing complexity of cyber threats, businesses must prioritize remote workforce security to safeguard sensitive data and ensure operational continuity.
Remote Work Cyber Security Challenges
The Covid-19 pandemic played a significant role in accelerating the transition to remote work on a global scale. For many employees, it was an entirely new experience, one that introduced considerable remote work security challenges. Numerous IT departments had days, rather than weeks, to implement security measures, often resulting in ad hoc policies. According to a report by Morphisec, nearly half of office workers were new to remote work when the transition occurred. This lack of experience with work from home, both on the employer and employee’s side, made it difficult to maintain cyber security measures outside of the organization’s traditional perimeters.
Cybercriminals quickly adapted, leveraging increased connectivity and the extended attack surface of home networks to target sensitive information. In a matter of months, cyberattacks surged; Morphisec reported over a 100,000 increase in weekly attacks between February and April 2020 alone. These figures highlight how remote work intensified cybersecurity challenges, emphasizing the urgent need for tailored remote work security measures.
Work From Home is Here to Stay
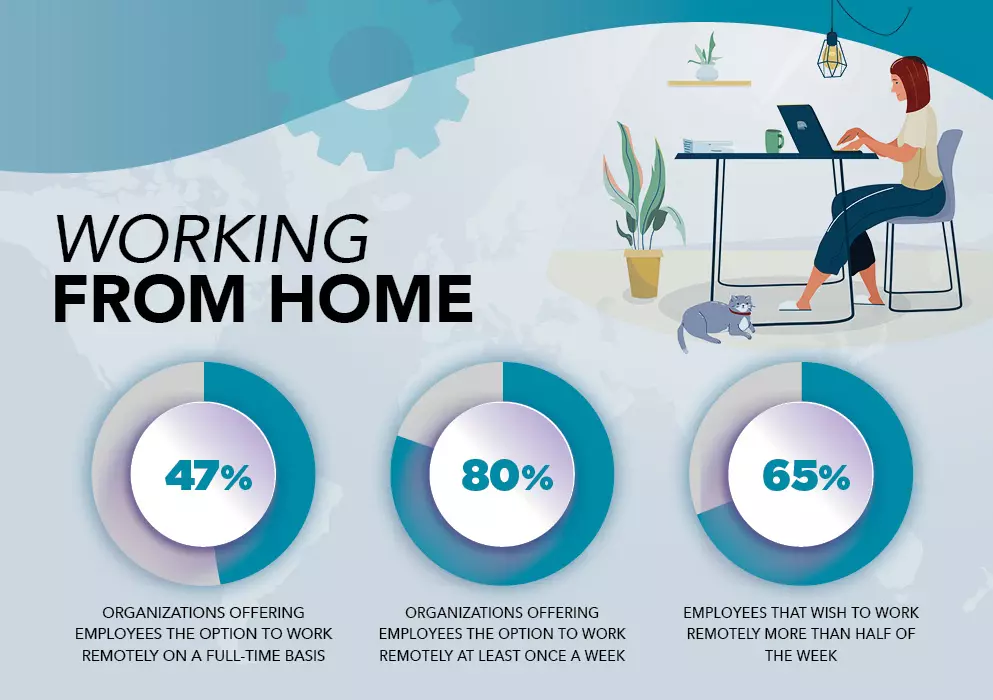
Many organizations have embraced the hybrid model, allowing employees to work from home either full-time or part-time. According to Gartner, 47% of organizations will give employees the choice to Work From Home on a full-time basis. Over than 80% will allow employees to Work From Home at least one day a week. This will likely be good news for many employees who enjoy remote work. In fact, 65% expressed a desire to work from home more than three days a week, according to a survey by Evolve IP. The same survey shows that 75% of employees feel more effective when working remotely. On average, they report a 31% increase in productivity.
Remote work cyber security has become a core priority for organizations striving to protect sensitive data and assets in this new reality.IT teams must implement robust remote work security policies and adaptive technologies to address the unique challenges of hybrid and remote work environments.
Common Security Vulnerabilities in Remote Work
After more than a year of adjusting to remote work, organizations have strengthened their remote work security policies. However, vulnerabilities persist. According to Evolve IP, 60% of employees believe cybersecurity measures still need improvement. In many cases, security policies lack proper enforcement; even when strict work-from-home guidelines exist, 25% of employees fail to follow them. This poses a significant remote work security risk, especially as personal devices often lack the robust security protocols necessary to protect sensitive data.
Personal Device Risks
Personal devices present a major remote work security risk due to their unmanaged status and lack of robust security measures. With 56% of employees using personal computers and 46% relying on personal mobile devices for work, these endpoints introduce significant vulnerabilities. Alarmingly, 60% of companies lack a clear acceptable use policy for personal devices, further exposing organizations to cyber threats.
This gap in security is particularly concerning because employees often represent the greatest cybersecurity risk. Even with protective measures such as Network Access Control (NAC), VPNs, and Intrusion Detection Systems (IDS), cybercriminals have found ways to bypass these defenses. Hardware-based attacks exploit the less physically secure environments in which remote work occurs, making remote workforce security a critical priority.

Evolving Remote Work Security Strategies
As remote work continues to expand, organizations must enhance their remote work security strategies to address new and emerging cyber threats. With more employees working remotely and in hybrid models, the number of entry points for cybercriminals increases. To safeguard sensitive data and ensure uninterrupted operations, companies should implement secure VPNs, multi-factor authentication (MFA), and endpoint protection. Additionally, regular employee training on remote work security best practices is essential to mitigate risks. By proactively adapting to these challenges, businesses can build a robust remote work cyber security framework to defend against evolving threats.
Hardware Security: The First Line of Defense in Remote Work Cyber Security
One of the biggest challenges in remote work security is the lack of control over device usage and the limitations of traditional security solutions. To mitigate these risks, enterprises must prioritize hardware security as the first line of defense. Sepio’s platform provides complete visibility into all hardware assets operating within the corporate infrastructure, across both USB and network interfaces. By analyzing the Physical Layer, Sepio detects and identifies all connected devices, ensuring their true identity is verified. This capability enables organizations to enforce hardware access control policies based on user roles and device characteristics, strengthening remote work security at its core.
When a device breaches pre-set security policies, Sepio automatically triggers a mitigation process that blocks the device. This proactive approach allows enterprises to minimize risks associated with remote work security at the earliest opportunity, eliminating the reliance on employees and ineffective security solutions for protection.
As telework becomes the new norm, security departments must ensure that the most efficient tools are deployed. Without them, enterprises are at a higher risk of falling victim to hardware-based attacks sooner rather than later.
Secure Your Remote Workforce Today
As remote work evolves, so should your cybersecurity strategy. Discover how Sepio’s platform can protect your organization from emerging threats. Gain complete visibility and control over every connected device to strengthen your remote work security.
Schedule a Demo to see how our hardware access controls, network monitoring, and endpoint protection can keep your team secure, productive, and resilient.






