Sepio’s NIST Cybersecurity Framework solution delivers complete visibility, real-time risk management, and regulatory compliance across IT, OT, and IoT environments. Empower your organization to secure all connected devices and maintain business continuity.
Traditional, traffic-based security solutions fail to cover the Physical Layer (Layer 1), resulting in inaccurate asset inventories, unaccounted-for vulnerabilities, and unidentified risks—all of which hinder cybersecurity efforts. This lack of visibility limits alignment with the NIST Cybersecurity Framework (CSF), as many required controls cannot be met. As a result, organizations experience weakened cybersecurity and resilience capabilities, increasing overall business risk.
Sepio’s Trafficless Network Security Solution provides full asset visibility without relying on traffic inspection. Unlike legacy solutions, it identifies and secures all hardware assets without analyzing network traffic or installing extra sensors—maintaining performance, resilience, and privacy.

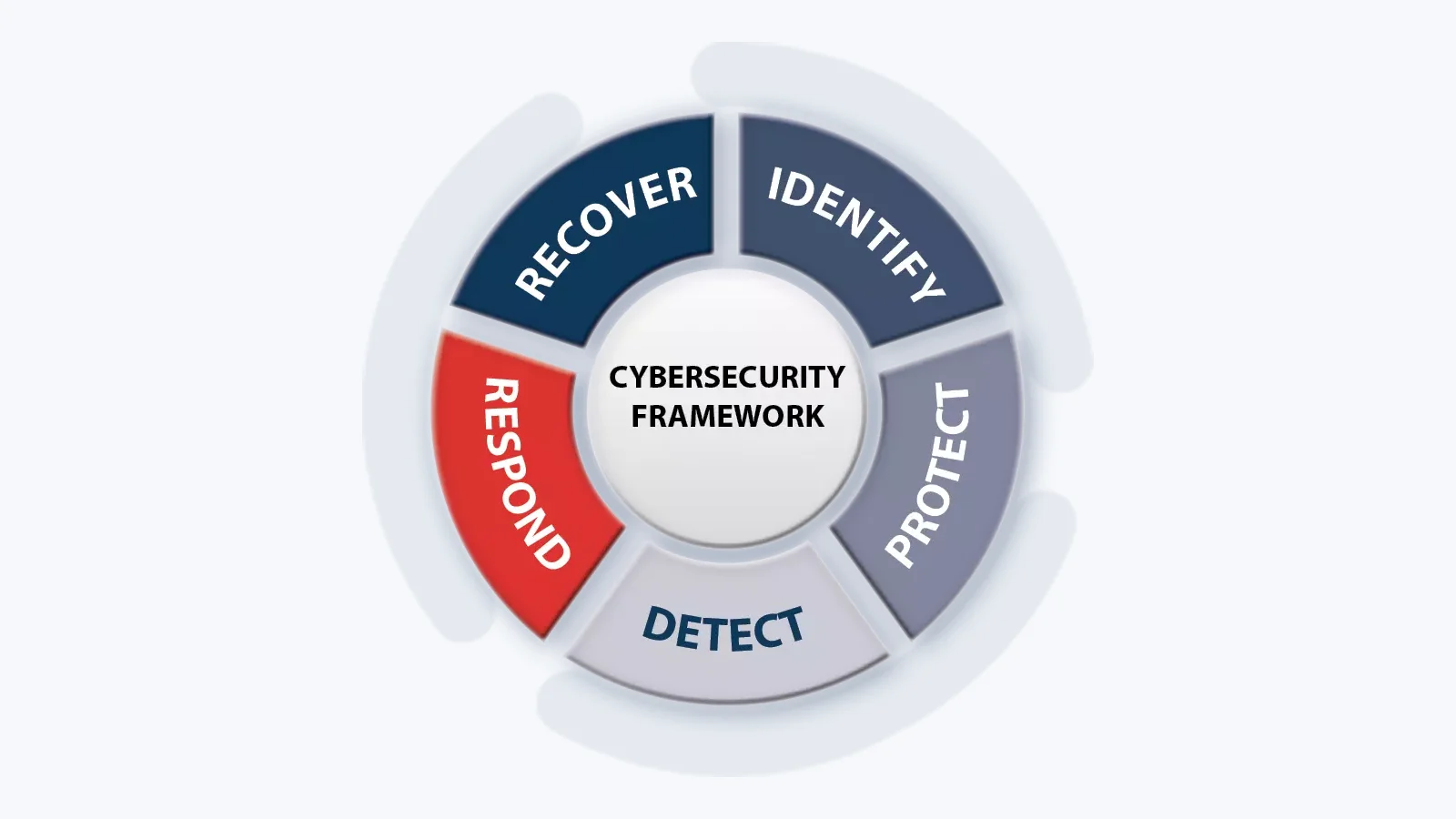
Sepio’s solution provides comprehensive asset visibility, helping enterprises fulfill many NIST Cybersecurity Framework (CSF) controls—from Identify to Respond. By leveraging physical-layer data, Sepio accurately detects and identifies all IT, OT, and IoT assets across USB and network interfaces, including managed, unmanaged, and hidden devices.
This advanced visibility enables organizations to:

With Sepio, organizations gain full visibility and control over IT, OT, and IoT assets, turning the NIST Cybersecurity Framework into actionable protection against cyber risks—Identify, Protect, Detect, and Respond in real time.
