In today’s interconnected IT, Operational Technology (OT), and Internet of Things (IoT) environments, seemingly harmless hardware devices can pose significant security risks. One such often-overlooked device is the unmanaged switch. These Ethernet switches may appear to be simple plug-and-play solutions, but they carry inherent vulnerabilities that can jeopardize an organization’s cybersecurity.
In this article, we will dive into the risks associated with unmanaged Ethernet switches, explore the vulnerabilities they introduce to networks, and discuss effective strategies for mitigating these risks to safeguard your network infrastructure.
Unmanaged Switch: Overview
An unmanaged switch is a basic networking device designed to connect multiple Ethernet devices within a Local Area Network (LAN). Unlike managed switches, an unmanaged switch lacks configuration options, meaning it operates as-is without providing visibility into network traffic or device management. While their simplicity makes them suitable for small networks or temporary setups, the security risks associated with them can be severe.
- Lack of Configuration: One of the key limitations of an unmanaged switch is the lack of configuration capabilities. This absence means network administrators cannot segment traffic or enforce security policies. Consequently, unmanaged ethernet switches are an unsuitable choice for environments that require advanced security controls and traffic management.
- Ease of Use: While an unmanaged switch is easy to set up and deploy, this convenience comes at the expense of security. Unmanaged switches do not offer features to control which devices can connect to the network or how devices communicate with each other. This lack of control opens the door to potential cybersecurity vulnerabilities.
The MITM Attack Vulnerability
An unmanaged switch can inadvertently create a separate, unmanaged link to the public internet bypassing the organization’s defense layers. When a malicious computer connects to this switch, it can establish a concealed link. This link can give the attacker full access to the organization’s IT network and data.
Such setups become fertile grounds for Man-in-the-Middle (MiTM) attacks. In these attacks, the attacker secretly intercepts the communication between two parties. They may also alter the messages, causing the parties to believe they are communicating directly.
- Bypassing Security Layers: A malicious computer connecting to an unmanaged switch can bypass the organization’s security layers, allowing unauthorized access to sensitive information.
- Data Interception: Man-in-the-Middle (MiTM) attacks can lead to stolen credentials, sensitive data leaks, and significant reputational damage. Organizations must recognize the importance of securing an unmanaged switch to protect against these threats.
MAC Spoofing and Reconnaissance
Moreover, unmanaged switches can be employed in the reconnaissance phase of MAC spoofing attacks. In MAC spoofing, attackers imitate a legitimate MAC address to bypass network security measures. The absence of management features in these switches makes detecting such activities challenging.
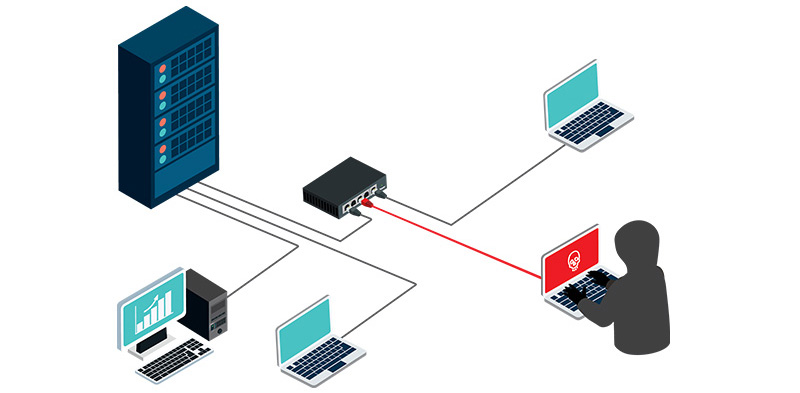
Challenges in Unmanaged Switch Detection
The subtlety of unmanaged switches lies in their lack of invisibility to traditional cybersecurity systems. These switches lack identifiable characteristics at layer 2 and above, making them and any device behind them undetectable. For instance, an unmanaged hub switch doesn’t have an associated MAC address, making it “MAC’less“.
Sepio’s Solution Unique Approach
Recognizing this silent threat, Sepio’s solution uses physical layer data obtained from the physical layer of the network infrastructure to identify MAC’less devices. By alerting the security teams about such risky configurations, organizations can take proactive measures to secure their network infrastructure.
- Physical Layer Visibility: Sepio monitors the network’s physical layer to detect MAC-less devices. This helps alert security teams to risky configurations. This proactive approach enables organizations to take necessary measures to secure their networks.
- Alerting Security Teams: Organizations can configure alerts to notify security personnel when an unmanaged ethernet switch is detected. This enables a rapid response to potential threats.
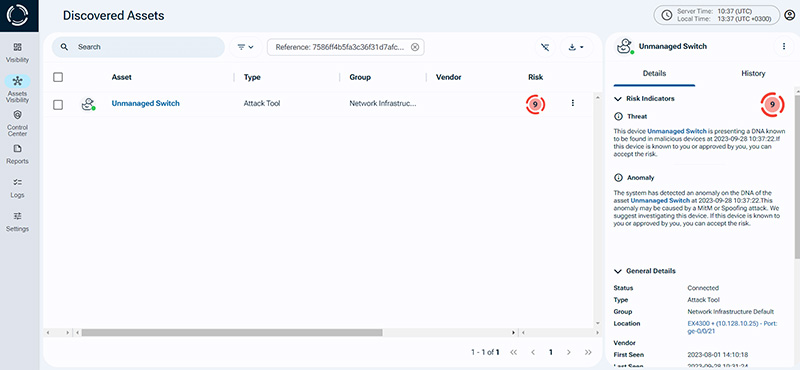
Closing the Security Gap of Unmanaged Switches
Unmanaged ethernet switches may seem simple, but they pose serious security risks. Their lack of configuration options and the potential for attacks like Man-in-the-Middle (MiTM) and MAC spoofing make them a silent threat to your network.
To mitigate these risks, it’s essential to use advanced detection tools like Sepio’s solution. By monitoring the physical layer and setting alerts, organizations can quickly identify and address unmanaged switch vulnerabilities. Don’t wait until it’s too late. Schedule a demo today and take the first step towards securing your network.




