Formula 1 (F1) cybersecurity refers to the measures and practices implemented within the Formula 1 racing industry to protect its digital assets, information, and infrastructure from cyber threats. As with any other industry, F1 organizations are increasingly reliant on digital technologies, analytics, and communication systems to gain a competitive edge in the highly competitive world of racing.
Formula 1 might be the most famous racing competition in the world. However, behind the scenes, the sport is based almost entirely on math and science. And, no, this does not diminish the sport’s “cool factor”. It makes Formula 1 racing one of the most innovative industries in the world – and how cool is that? But, with this comes numerous concerns to the cybersecurity world, including F1 cybersecurity.
The Science and Math of Racing
Racing teams calculate every move in an F1 race, and every millisecond shapes the overall outcome. In Formula 1 racing, performance is everything. And to outperform competitors, innovation is a necessity; materials, aerodynamic design, and even the driver’s clothing are a few of the areas in which there are constant improvements. Even during the race, engineers are looking for ways to improve the car’s performance while keeping a watchful eye on F1 cybersecurity.
How Do They Do It? Data.
Each F1 car carries around 150–300 sensors to collect data. During a single Grand Prix weekend, a car generates roughly 300MB of performance records. The data is analyzed in real-time to ensure that the car performs at its optimum performance level. The data transmitted by the sensors to the engineering staff can show things invisible to the human eye that might impact performance. As such, engineers make real-time decisions to improve a car’s performance and the overall race outcome. But the data collection extends beyond the race itself. Each week, the factory produces 5–10TB of data, and engineers analyze most of it to drive innovation. With an F1 racing team generating so much data – and such data being one of its greatest assets – F1 security becomes crucial, as the team is a valuable target for various hardware attacks.
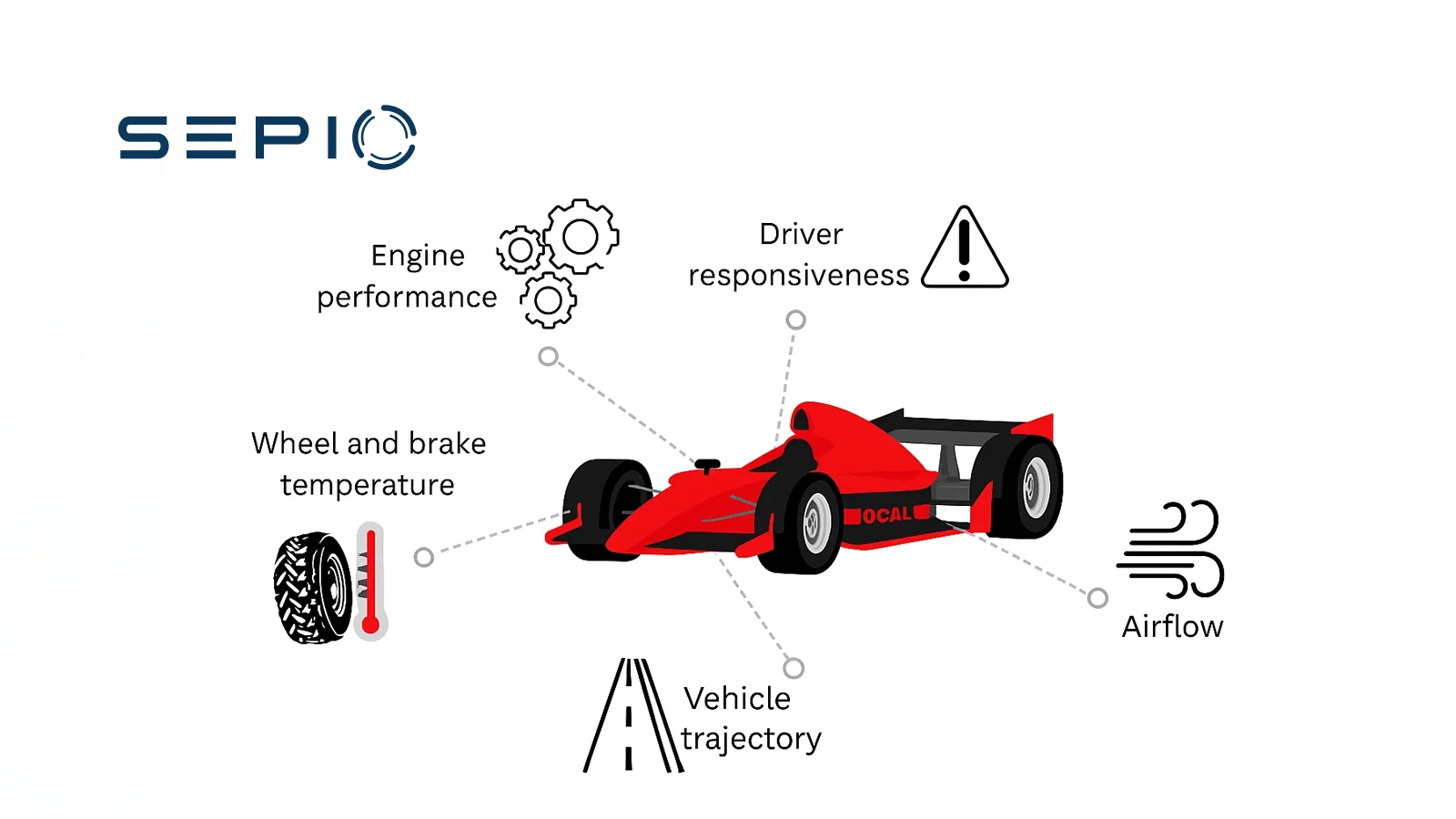
F1 Cybersecurity: Protecting Against Data Theft
Primarily, there is the threat of espionage in the form of data theft. F1 racing is known to be a highly competitive sport, and not always in a good way. The sport is often the subject of intense rivalry. It is the latter that can be a significant threat when it comes to data security and espionage. With such a vast amount of data collected for innovation and performance improvement purposes, a rival competitor might seek to steal such data or intellectual property for its own performance improvements, as was the supposed intention behind the Spygate controversy.
In other cases, an adversary might seek to disrupt the operation, whether that be disruption to production, to data analysis, or even the car itself. Attacks such as DDoS and ransomware can halt productivity at the factory by rendering systems and their data temporarily inaccessible. This is especially harmful when it comes to real-time data analysis since every second counts. In 2014, a trojan virus impacted the Marussia F1 team, resulting in a loss of an entire day’s worth of testing. In a more chilling scenario, a hacker could alter the data used to re-engineer vehicles in order to harm the car’s performance (Car Computer Security).
F1 Cybersecurity: Protecting Critical Data
When it comes to financially motivated cybercriminals, sensitive records become a prime target. Cybercriminals sell stolen information on the dark web for profit, and data and intellectual property from an F1 organization raise the monetary reward significantly, making the team an appealing target. Simple business information such as personal records and financial statements belonging to a racing constructor can be enough for a bad actor to reap significant monetary benefits. Furthermore, the large budget of F1 teams makes them an attractive target for a ransomware attack. And the critical role that data plays in F1 racing increases the chances that the victim team will pay the ransom, underscoring the importance of robust F1 cybersecurity measures.
F1 Cybersecurity Challenges
It is not simply the substantial amount of data that a racing operation generates that puts it at risk. The Formula One World Championship requires the teams to relocate almost weekly to participate in the events held in more than 20 countries. Such global movement greatly expands the attack surface as data is transmitted internationally. Moreover, countries impose different cybersecurity regulations. The threat actors vary from country-to-country, which play a significant role in determining the threat landscape. With less stringent regulations in certain countries and regions, it is easier for an attacker to target an F1 team, while different threat actors pose different levels of risk based on their capabilities. The security department of the F1 team has a big task at hand to ensure the maintenance of the team’s security levels at any and all locations, emphasizing the critical role of F1 security in safeguarding the team’s assets.
Big Name, Big Target
F1 racing names are recognized worldwide, from the drivers to the teams and constructors. Any attack on an F1 organization would attract significant attention. Such recognition can be a motivating factor for some bad actors. In some instances, the attacker wants glory and fame for themselves. In others, the perpetrator might seek attention for a more specific reason. A successful cyberattack can highlight the security flaws of the victim team, harming its reputation.
Earlier this year, the Williams F1 team abandoned the launch of its new FW43B F1 car following a hack on the augmented reality app that would reveal the vehicle. Since many teams’ constructors also produce commercial vehicles, an attack can harm sales. Alternatively, a malicious actor might want to bring attention to a specific cause or movement, particularly one against an F1 team. For example, an environmentalist might target an F1 team to raise awareness of the environmental impacts of racing. In other instances, attacking an F1 team can simply be a strategic move by a hacktivist to bring attention to a completely unrelated issue. Whatever the reason, an attacker can be sure that targeting an F1 team will generate press coverage and public discourse, emphasizing the need for robust F1 cybersecurity measures to mitigate and manage these risks.
Hardware-based Attacks
Attackers are more frequently turning to hardware tools to conduct their malicious activity. These rogue devices are extremely threatening due to their covert nature. Network Implants sit on the Physical Layer, which is not covered by any existing security software solutions. This allows the device to go undetected. Spoofed peripherals, on the other hand, impersonate legitimate HIDs and are therefore not detected as malicious. Depending on the device’s capabilities, an attacker can conduct a range of attacks. This includes data theft, network packet sniffing, man in the middle attacks (MiTM), and more.
Formula 1 constructors are an attractive target for a hardware-based attacker. Each team generates vast amounts of data and operates a global network. The constant use of data to improve performance requires departments to communicate and share access. This expands the attack surface as there are more entry points for the attacker. Device visibility is imperative for an F1 team to reduce the chances of a successful hardware attack.
Ultimately, when it comes to Formula 1 racing, it is not just the cars racing against each other. The constructors are in a race with attackers to ensure they protect their data and cars before a malicious actor can get their hands on them. But, unlike F1, the race does not end at the checkered flag. It continues in the world of F1 security, where constant vigilance is necessary to safeguard against potential threats.






