Cybersecurity regulatory compliance refers to the adherence to laws that govern the protection of data from unauthorized access, disclosure, alteration, and destruction. Compliance with cybersecurity regulations is crucial for organizations to ensure the security and privacy of sensitive information. Maintain trust with customers, and avoid legal and financial consequences.
Key Aspects Cybersecurity Compliance
Cybersecurity compliance involves adhering to various laws, regulations, and standards designed to protect digital data and systems from cyber threats. Here are the key aspects of cybersecurity compliance:
Understanding Applicable Compliance Regulations: Identify and understand the specific cybersecurity regulations that apply to your organization based on factors such as industry, geographic location, and the type of data you handle.
Risk Assessment and Management: Conduct regular risk assessments to identify potential cybersecurity vulnerabilities, threats, and risks to your organization’s information systems and data. Develop and implement risk management strategies to mitigate these security risks effectively.
Data Protection and Privacy: Implement measures to protect sensitive data, including encryption, access controls, and data loss prevention technologies. Ensure compliance with regulations governing data privacy, such as GDPR or HIPAA, by obtaining necessary consents, limiting data collection and retention, and providing individuals with rights over their data.
Cybersecurity Controls and Safeguards: Implement appropriate technical and organizational security controls to safeguard against cyber threats, including malware, phishing, insider threats, and unauthorized access.
Documentation and Compliance Reporting: Maintain accurate documentation of cybersecurity policies, procedures, and controls to demonstrate compliance with regulatory requirements.
Vendor and Third-Party Management: Assess the cybersecurity posture of third-party vendors and service providers that have access to your organization’s systems or data.
Identify Regulatory Compliance Gaps
One of the common use cases raised by Sepio’s customers is for those who operate in highly regulated environments. The need to comply with multiple regulations. Whether it’s healthcare, federal, critical infrastructure, or financial, there is a genuine challenge in ensuring there are no cybersecurity regulatory compliance gaps.
An entity following NDAA section 889b must verify that it does not use any hardware assets from banned Chinese vendors. To comply with this requirement, a complete and trusted asset inventory should be available and up-to-date at any given time.
From NDIA website:
The 2019 National Defense Authorization Act’s Section 889 prohibits the federal government, government contractors, and grant and loan recipients from procuring or using certain “covered telecommunication equipment or services”. The specified equipment is produced by Huawei, ZTE, Hytera, Hikvision, and Dahua, along with their subsidiaries. When it serves as a “substantial or essential component of any system” or is considered critical technology within a system.
Government stakeholders and contractors need to inventory their telecommunication equipment. Evaluate their supply chain and acquisition procedures in order to identify prohibited equipment in their network infrastructure.
This is a difficult task for legacy ITAM tools which fail to discover and fully identify the manufacturers of all devices in all network environments (IT, OT, IoT). Some organizations use multiple tools and patch together inventory reports which results in visibility gaps. Additionally, white-labeled and private-labeled devices may create further gaps in cybersecurity regulatory compliance.
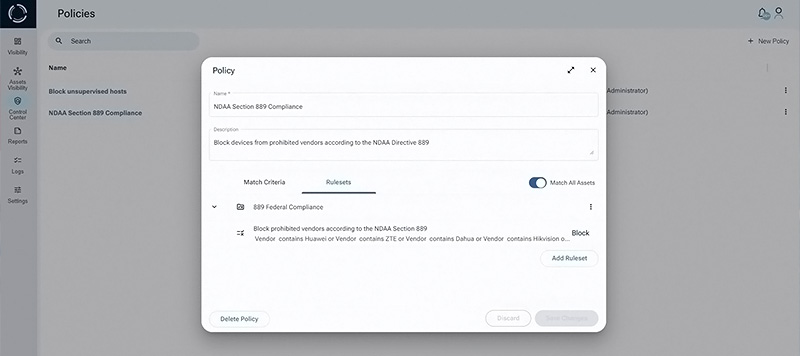
How Sepio’s Helps with CyberSecurity Regulatory Compliance Gaps
Sepio‘s innovative Asset Risk Management (ARM) solution proves to be the answer to these cybersecurity regulatory compliance gaps challenges:
Comprehensive Hardware Inventory: Provides a complete and up-to-date inventory of all hardware assets across the organization. Including all wired and wireless Ethernet-connected devices, USB peripherals, and internal hardware Bill of Materials. This asset inventory serves as the foundation for cybersecurity regulatory compliance efforts.
Cybersecurity Regulatory Compliance Mapping: Maps each hardware asset to relevant compliance regulations. Such as GDPR, HIPAA, and NDAA section 889b. This enables organizations to identify which regulations specific hardware affects and to prioritize compliance efforts accordingly.
Continuous Monitoring: Offers continuous monitoring of hardware assets, flagging any unauthorized or suspicious devices. This real-time monitoring ensures that cybersecurity regulatory compliance efforts are ongoing and adaptive.
Closing CyberSecurity Regulatory Compliance Gaps
Demonstrated Compliance: Organizations can confidently demonstrate cybersecurity regulatory compliance with GDPR, HIPAA, and NDAA 889b during audits. Assuring regulators and government contract evaluators of their commitment to security and privacy.
Reduced Risk: The risk of data breaches and associated legal consequences decreases significantly due to improved hardware security measures.
Operational Efficiency: With a streamlined hardware asset management process, Sepio’s platform improves operational efficiency and reduces the costs associated with cybersecurity regulatory compliance efforts.
By addressing their hardware assets visibility challenges with Sepio’s solution, customers not only achieve compliance at a lower cost but also enhance their overall cybersecurity posture.




