What is IoT Security?
IoT security refers to protecting smart, internet-connected devices from threats and unauthorized access. These devices are widely used in homes, businesses, and critical infrastructure. Since they often handle sensitive or valuable data, ensuring their security is essential. Effective security measures prevent unauthorized access and help maintain data privacy.
As more IoT devices come online, their role in daily operations continues to grow, automating tasks, collecting data, and transforming how we interact with our environments. It is no surprise that over 30% of connected devices in a typical company are IoT, making them a big target. Without proper protection, these devices can become gateways for cyberattacks, data breaches, and malware infections.
Effective IoT Security ensures device integrity, privacy, and trust across all layers of connectivity.
Why Are IoT Devices a Target for Cyberattacks?
Hackers actively target IoT devices due to their weak security configurations, infrequent updates, and broad network reach. According to Threatpost, IoT attacks doubled in the first half of 2021, proving how rapidly these vulnerabilities are being exploited.
Since many IoT devices lack strong authentication and encryption mechanisms, they often serve as entry points into corporate networks. Once compromised, attackers can move laterally, impacting critical systems or stealing sensitive data.
For a technical overview, see IETF RFC 8576, which outlines IoT security challenges and threat considerations.

IoT Device Security Risks
The widespread use of IoT has created new attack surfaces. These devices gather and transmit personal, financial, and operational data, making them valuable targets.
Attackers exploit vulnerabilities to gain control of IoT devices, launch DDoS attacks, install malware, or use them for state-sponsored espionage. As IoT becomes deeply integrated into IT environments, these risks multiply.
Common IoT device security risks include:
- Weak or default passwords
- Lack of firmware updates
- Insecure network connections
- Unmonitored third-party devices
These factors highlight why strong IoT cybersecurity practices, including software updates, network monitoring, and hardware access control, are essential.
Network and IoT Security
As more IoT devices connect to corporate networks, ensuring IoT Network Security becomes increasingly complex. Every new device represents a potential network entry point.
A simple example: a connected coffee machine or printer might seem harmless, but if compromised, it can allow attackers to infiltrate your network.
To reduce these risks, it’s important to use strong network controls, like firewalls and network segmentation. These tools limit what each device can do, helping stop threats and block attackers from moving across the network.
Remote Work and IoT Security
With more people working from home, IoT device security now matters outside the office too. The average home has about 25 connected devices, including smart TVs, cameras, fridges, and security systems. Each device can potentially serve as an entry point for hackers.
As more devices go online, the need for strong IoT security grows, both at work and at home. Since these devices are everywhere, keeping them safe is a shared job for everyone.
IoT Device Visibility
Even with security tools and network controls, finding every connected IoT device is still a challenge. Traditional endpoint and network tools often miss or misidentify these devices, leaving blind spots that attackers can use.
Traditional solutions like NAC, IDS, and IoT security platforms help, but they often miss what’s happening at the physical layer. This gap means rogue devices to go undetected, putting both IoT hardware and network security at risk. That’s where Sepio’s Asset Risk Management (ARM) platform makes a difference.
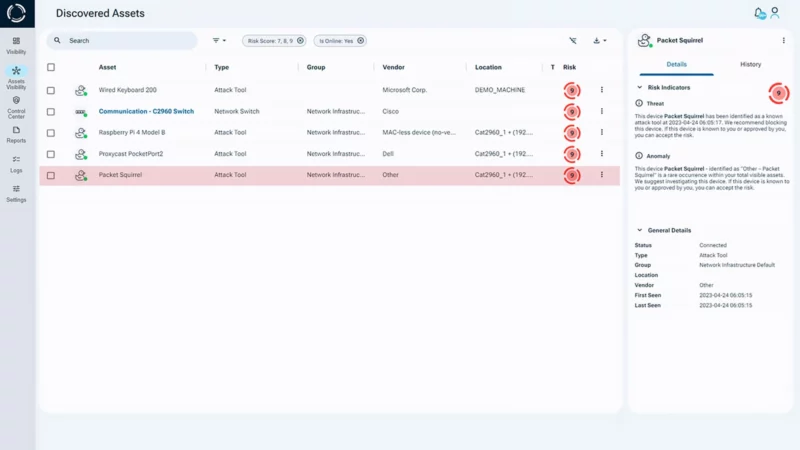
Many IoT devices lack basic security and are often overlooked because they appear harmless. However, these devices frequently have hidden vulnerabilities that increase risk over time. As threats grow more sophisticated, it is crucial to strengthen network defenses to prevent attacks.
Sepio’s Approach to IoT Security
Sepio’s Asset Risk Management (ARM) platform helps businesses protect their IoT devices by showing what’s connected at the physical layer.
It creates a digital fingerprint for every IT, OT, and IoT detecting and identify connected assets accurately. With built-in policy enforcement and Rogue Device Mitigation, it can quickly block unauthorized or rogue hardware, keeping the network safe from hardware attacks.

With Sepio’s platform, organizations can better protect their networks and improve IoT device security. It shows all connected devices clearly, helping secure each one and strengthen overall IoT cybersecurity.
Key Capabilities of Sepio’s IoT Security Platform
Sepio’s trafficless CPS Protection Platform secures IoT devices and networks by discovering all connected assets at the physical layer. With exceptional visibility and automated risk blocking, it strengthens security across IT, OT, and IoT environments.
Unmatched Visibility
- Detects all IoT assets using physical-layer data, including shadow and spoofed devices.
- Works with existing tools for enhanced visibility and return on investment.
IoT Device Security
- Identifies assets via Asset DNA, regardless of OS or identifiers.
- Immune to spoofing and false alarms.
- Enforces granular policies based on risk, vendor, or asset type.
IoT Network Security
- Blocks malicious hardware tools in real time.
- Monitors device behavior with automated risk scoring.
- Secures the network from hardware-based attacks.
Secure Your IoT Devices and Protect Your Network
Securing IoT environments starts with full visibility. Sepio’s trafficless CPS Protection Platform helps organizations strengthen IoT Security by discovering every connected asset at the physical layer.
By combining visibility, automation, and risk-based blocking, Sepio delivers comprehensive IoT cybersecurity that keeps your network protected from evolving threats.
Talk to an expert to learn how Sepio can help safeguard your IoT devices, improve asset visibility, and protect your network from hardware-based attacks.






