What is Remote Work Security?
Remote work security means protecting remote work setups from cyber threats. Employees work from many places and use both company and personal devices. This has made cybersecurity harder and more complex.
As remote work security grows into a global priority, organizations must tackle new risks. Whether employees use personal (BYOD) or company devices, unsecured connections and unknown peripherals raise breach risks. Because cyber threats are getting more complex, businesses must focus on securing their remote workforce to protect sensitive data and keep operations running smoothly.
Remote Work Cyber Security Challenges
The Covid-19 pandemic sped up the global shift to remote work. For many employees, remote work was a completely new experience, bringing many security challenges. IT teams had days, not weeks, to set up protections, often leading to quick, temporary policies. According to a Morphisec report, almost half of office workers were new to remote work during this time. This lack of experience, from both employers and employees, made it hard to keep security outside the usual company boundaries.
Cybercriminals quickly took advantage of the shift to remote work. They used the increase in connectivity and the weaker security of home networks to go after sensitive data.
In just a few months, cyberattacks surged. According to Morphisec, there were over 100,000 more attacks per week between February and April 2020. These numbers show how remote work made cybersecurity harder, and why it’s urgent to have security tools built specifically for remote work environments.
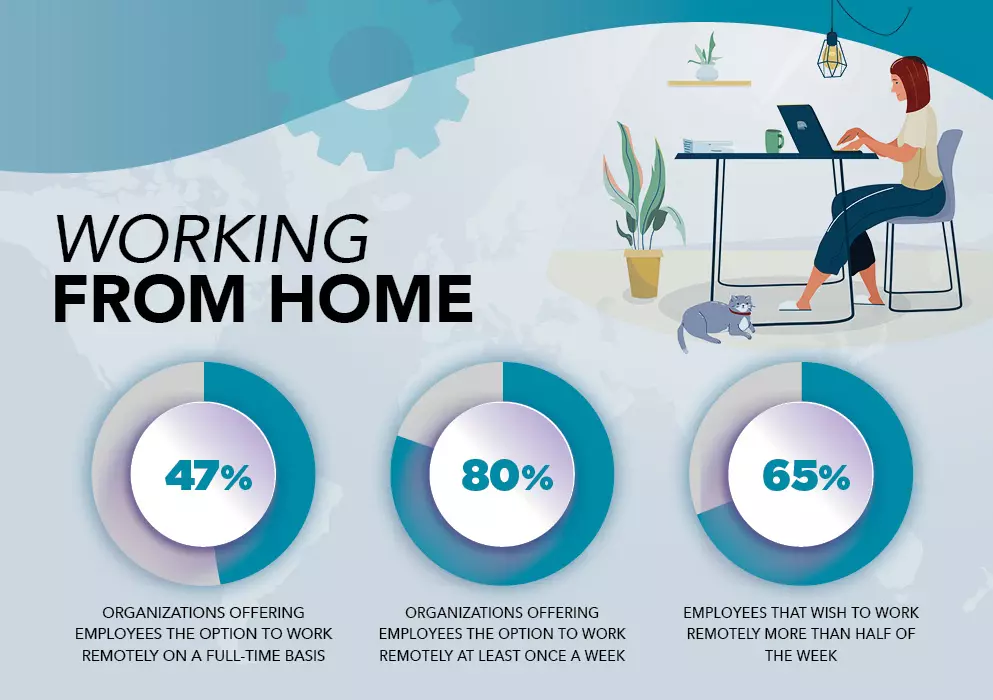
Work From Home is Here to Stay
Many organizations have adopted the hybrid work model, letting employees work from home full-time or part-time. According to Gartner, 47% of organizations will allow full-time remote work. Over 80% will let employees work from home at least one day a week. This is good news for many who enjoy remote work. In fact, a survey by Evolve IP found that 65% want to work from home more than three days a week. The same survey shows 75% feel more effective when working remotely. On average, employees report a 31% boost in productivity.
Remote work security is now a top priority for organizations that want to protect sensitive data and systems.
To meet the unique challenges of hybrid and remote work, IT teams must create strong security policies and use flexible, modern technologies that adapt to changing threats.
Common Security Vulnerabilities in Remote Work
After more than a year of adjusting to remote work, organizations have improved their security policies. However, vulnerabilities still remain. According to Evolve IP, 60% of employees believe cybersecurity measures need further improvement. In many cases, security policies are not properly enforced. Even when strict work-from-home guidelines exist, 25% of employees do not follow them. This creates a significant remote work security risk, especially since personal devices often lack strong security protocols needed to protect sensitive data.
Personal Device Risks
Personal devices are a major security risk in remote work because they’re often not managed by the company and lack strong protection.
Around 56% of employees use personal computers, and 46% use personal mobile devices for work. These devices create serious vulnerabilities.
On top of that, 60% of companies don’t have a clear policy for how personal devices should be used. This gap makes it even easier for cyber threats to slip through.
This gap in security is particularly concerning because employees often represent the greatest cybersecurity risk. Even with protective measures such as Network Access Control (NAC), VPNs, and Intrusion Detection Systems (IDS), cybercriminals have found ways to bypass these defenses. Hardware-based attacks exploit the less physically secure environments in which remote work occurs, making remote workforce security a critical priority.

Evolving Remote Work Security Strategies
As remote work continues to grow, organizations must strengthen their security strategies to face new threats.
With more employees working remotely or in hybrid setups, the number of ways cybercriminals can get in has increased.
To protect sensitive data and keep operations running smoothly, companies should use tools like secure VPNs, multi-factor authentication (MFA), and endpoint protection.
In addition, regular employee training on remote work security best practices is vital to reduce risks.
By taking these steps, businesses can build a strong remote work cybersecurity framework to defend against evolving threats.
Hardware Security: The First Line of Defense in Remote Work Cyber Security
One of the biggest challenges in remote work security is the lack of control over device use and the limits of traditional security tools. To reduce these risks, companies must make hardware security their first line of defense. Sepio’s platform gives full visibility into all hardware assets in the corporate network, including USB and network devices. By analyzing the Physical Layer, Sepio detects and identifies every connected device, confirming its true identity. This lets organizations enforce hardware access policies based on user roles and device features, making remote work security stronger from the ground up.
When a device breaks pre-set security policies, Sepio automatically starts a mitigation process that blocks the device. This proactive method helps companies reduce remote work security risks as early as possible. It removes the need to rely on employees or ineffective security tools for protection.
As telework becomes the new norm, security teams must deploy the most effective tools. Without these tools, enterprises face a greater risk of hardware-based attacks, often sooner rather than later.
Secure Your Remote Workforce Today
As remote work evolves, your cybersecurity strategy must evolve too. Discover how Sepio’s platform protects your organization from emerging threats. Gain full visibility and control over every connected device to boost your remote work security.
Schedule a Demo to see how our hardware access controls, network monitoring, and endpoint protection keep your team secure, productive, and resilient.






