What is ATM Jackpotting?
ATM Jackpotting is a type of cyber-physical attack where criminals force an ATM to dispense all of its cash. Just like hitting the jackpot on a slot machine. By exploiting software vulnerabilities or gaining physical access, attackers can hijack the machine’s operations.
How ATM Jackpotting Works?
In ATM Jackpotting Attacks, the hackers usually gain access to the ATM’s software or hardware, either through physical manipulation or by exploiting vulnerabilities remotely. Once they are in, they can send commands to the ATM to make it dispense cash, just like that.
Money Doesn’t Grow on Trees
We’ve all heard the saying: money does not just appear, it takes hard work to earn it. However, what if that is not always true? In recent years, cybercriminals have used jackpotting attacks on ATMs to prove otherwise. These attacks show that, yes, money can just appear. And no, it does not take long hours or effort, just a few minutes.
ATM jackpotting is a highly attractive method for cybercriminals looking for quick cash. After all, ATMs are essentially metal boxes filled with money. It is no surprise they are frequent targets. A successful attack can bring instant and significant rewards. With over 3.5 million ATMs worldwide, hackers have no shortage of targets. And for many, ATM Jackpotting is the most direct way to attack.
How ATMs Provides a Attack Surface?
ATM Jackpotting is a type of logical attack that instructs the machine to dispense cash. Such attacks have become more frequent. With the European Association for Secure Transactions (EAST) reporting a 269% increase between 2019 and 2020.
The worldwide presence of ATMs means jackpotting attacks are a global threat. For instance, in Europe, Diebold Nixdorf, a leading ATM manufacturer, issued an alert warning about the rising number of jackpotting attacks in 2020. More recently, two individuals were arrested for ATM jackpotting attacks in Europe which saw them steal over $273,000. Meanwhile, in the United States, the Secret Service also issued a warning regarding the growing threat of jackpotting attacks.
How ATM Jackpotting Attacks Occur?
ATM jackpotting attacks occur through the use of ATM jackpotting software or by utilizing a black box. Both methods require physical access to the machine and the use of hardware attack tools, known as rogue devices. These rogue devices often include BadUSB tools, which are designed to bypass traditional endpoint solutions and device controls based on Vendor ID/Product ID detection or broad categories.
In many cases, hackers use simple flash drives to carry out harmful actions. These USB attack tools can inject keystrokes or run malicious commands. Surprisingly, they are often sold online for under $100, they are powerful enough to bypass most security controls. Once connected, they can force the ATM to dispense cash or give hackers access to the system.
These tools are a serious threat because they can bypass security protocols. Once connected, hackers use them to exploit system weaknesses. This can trigger a jackpotting event, where the ATM dispenses large amounts of cash without approval. In the process, the machine’s integrity is completely compromised.
ATM Malware
ATM Malware are a serious cybersecurity threat. Malware is short for “malicious software,” designed to infiltrate, damage, or gain unauthorized access to computer systems or networks. In an ATM Jackpotting attack, the attacker inserts a USB device ridden with ATM specific malware, such as CutletMaker or Ploutus D, into the ATM’s USB port. The malware instructs the machine to dispense cash which the hacker later collects. Ploutus malware, which first appeared in Mexico in 2013, has generated a loss of more than $450 million globally.
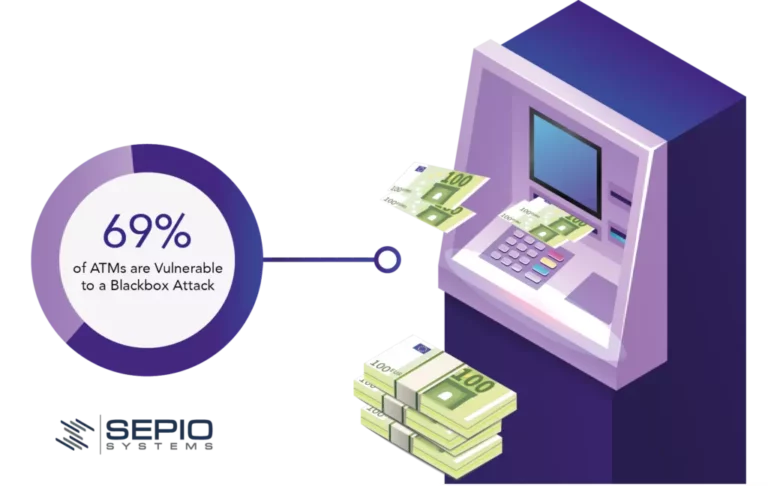
Black Box Attack
The hackers attaches a black box, typically a Raspberry Pi device, to the ATM’s internal cash dispenser. The device sends commands from the hacker to the cash dispenser, forcing it to release money. The hacker, or a accomplice, swiftly comes to pick up the cash.
According to research by Positive Technologies, a staggering 69% of ATMs are vulnerable to Black Box Attacks, highlighting the widespread risk posed by this technique.

ATM’s Lack Sufficient Physical Protection
To carry out a jackpotting attack, hackers need physical access to the ATM. They do this by opening the machine’s casing or using special tools to reach its internal components. However, this is not a major challenge, most offsite ATMs lack strong physical protection. Once inside, hackers install malware or manipulate the ATM’s hardware to take control. Although CCTV or public surveillance may be present, these are often minor obstacles that can be easily avoided.
Hackers not only go unnoticed, they use devices that work in secret. ATM jackpotting hardware tools operate at the Physical Layer, which cyber security solutions can’t see. Without visibility at this level, when a rogue device is inserted into an ATM, no security alarms are triggered. If nothing stops these hackers and their tools, ATM jackpotting become a real threat.
How to Protect Your ATMs from Jackpotting Attacks?
Heavy spending on cybersecurity should bring a high return on investment. Yet cyber security gaps limit this, especially in the face of threats like malware or black box attacks used in ATM Jackpotting.
Sepio’s Asset Risk Management (ARM) platform fills the gaps in network asset visibility. Its deep insight ensures no device goes unmanaged. The platform finds, tracks, and controls all IT, OT, and IoT devices. This helps you get the most out of your cybersecurity tools.

Sepio’s seamlessly integrating with existing solutions such as NAC, EPS, SIEM, and SOAR enhancing protection against threats like ATM Jackpotting. Additionally, Sepio’s policy enforcement mechanism and Rogue Device Mitigation capabilities instantly block any unapproved or rogue hardware. In doing so, Sepio’s enables a Zero Trust Hardware Access (ZTHA) approach which stops ATM Jackpotting at the first line of defense.
Sepio’s EndPoint and Network Security
Sepio’s patented technology gives you full control and visibility of your assets at the Physical Layer. It removes the need for traffic monitoring and helps you find and verify both known and unknown network assets. By assessing risk, you can focus on the highest-risk assets, keeping your operations running without any blind spots.
Sepio has successfully detected and blocked rogue devices at financial institutions. Give us just 24 hours to show you how we can secure your ATMs and stop you from becoming an attacker’s next slot machine.
Mitigate ATM Jackpotting CyberSecurity Risks
Schedule a demo. It will help you understand how to use Sepio’s patented technology to gain control of your asset risks