USB Attacks
USB Attacks are among the most covert and ignored cyber security threats facing organizations today. In an age dominated by digital transformation, hackers exploit weaknesses in USB devices or the USB protocol to compromise information security and gain not authorized network access. These sophisticated USB attack tools have evolved significantly, presenting serious risks to data integrity. As a result, the need for comprehensive USB cyber security solutions has never been more essential.
USB Attacks have also appeared during penetration testing (PT) completed for some of our customers. These tests often highlight gaps in incident response procedures and security policies. Spoofed USB devices used in PTs reveal how easily hackers can bypass traditional defenses, showing the critical importance of security awareness programs and effective cyber security training.
What are USB Attacks?
USB attacks often come from harmful devices called BadUSB. These devices can look innocent, like regular USB dongles, USB-C power adapters, or even parts of docking stations. Some of them can record what you type or steal login details. Their abilities are dangerous and wide ranging. They do not just install malware. Even without admin rights, they can steal sensitive data, quietly extract information, and change files or system setups.
One example of this threat is the USB Rubber Ducky. It looks like a normal keyboard but is actually a USB attack tool. It spoofs its Vendor ID, Product ID and ClassID to appear safe. Despite its safe name, it can be programmed to launch cyber attacks. Because it acts like a keyboard, it can bypass many security controls. This allows hackers to perform harmful actions such as installing malware, stealing sensitive data, or even taking full control of your system. That’s why practicing good cybersecurity habits is crucial. Always be careful when connecting USB dongles you don’t know.If you find a USB stick lying around or someone gives you one, it could be a USB drop attack, so think twice before plugging it in.


The Shortcomings of Today’s USB Security
USB attacks work by changing device firmware to do harmful things, like stealing data, loading malware, or taking over systems. These attacks are hard to detect because they act like normal devices. As a result, they often are not noticed, leaving organizations exposed to serious cybersecurity risks.
Existing cybersecurity mechanisms lack sufficient capabilities to effectively counter these hidden hardware-based attacks. Endpoint Detection and Response (EDR) solutions, while advanced, primarily focus on finding and responding to software-based payloads started by USB attacks. While successfully handling, legitimate USB dongles, USB sticks, USB cameras and mobile phones, they consistently fail to monitor the subtle events of malicious USB tools (BadUSB) being connected or disconnected from host systems. This is a cybersecurity risk that leaves organizations vulnerable to USB attacks.
A automatic security measure, adopted by many organizations, is sealing off all USB ports. Yet, this strategy is fraught with weaknesses:
Ubiquity of USB-C
With the adoption of USB-C power supplies in modern computer, merely sealing off USB ports doesn’t protect systems from USB drop attacks.
USB-C connectors are now used for various functions including power and data transfer. Because of this, completely seal off USB ports is not practical. Many modern electronics use USB-C for charging and connectivity. Turning off USB ports completely would prevent them from functioning properly.
Operational Disruption
Blocking USB functions can sometimes cause problems by stopping real peripherals like keyboards or mice from working. This is especially common in work-from-home (WFH) setups, where users often rely on personal USB hardware.
These vulnerabilities highlight the need for smarter, more balanced cybersecurity solutions. Organizations must adopt a layered approach that effectively blocks USB-based threats while still allowing trusted USB devices to operate safely and without disruption.
USB Security Solution
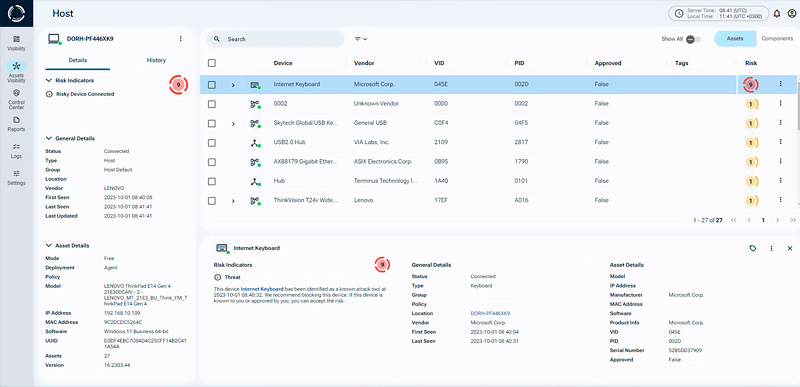
To fight these threats, advanced tools like Sepio’s platform offer a comprehensive approach to detecting and preventing USB-based attacks. Sepio provides complete visibility into all hardware assets across the organization, identifying potential risks and blocking malicious USB activity
Sepio goes deeper by checking the Hardware Bill of Materials (HBOM). It identifies the physical details of every device at the hardware level the moment it connects. This lets Sepio discover and profile every peripheral, including USB devices that may be hidden attack tools, even if they are inside legitimate USB devices.
Sepio’s Cyber Physical Security Platform, gives control over both known and unknown assets. It detects and block risks instantly, at any scale and from any location. Using a patented, physical layer approach, Sepio delivers clear, reliable insights, helping IT and security teams to identify and manage assets faster than ever before.
How to Protect your Organization from USB Attacks
USB-based cyber attacks are getting smarter and harder to spot. That’s why it’s important to take action before it’s too late:
- Train your team. Teach employees about USB threats and how hackers use tricks like social engineering.
- Set clear rules. Use strong hardware and software security policies.
- Use smart tools. Platforms like Sepio’s can help detect threats and respond in real time.
By handling USB-based threats with smart solutions, organizations can better protect themselves from many types of cyber risks. This helps keep systems safe in a world where cyber threats are always changing.
Strengthen Your Defenses Against USB-Based Attacks
USB attacks and other USB threats, are a serious danger to organizations. BadUSB hardware attack tools can look like real devices, but they are designed to cause harm. These hardware attacks can break into your systems and put your entire IT setup at risk.
Don’t leave your organization vulnerable to USB attacks. See every known and shadow asset in your ecosystem and protect against potential USB threats. Request a demo to learn more about USB security on your network.




