OSI Model Physical Layer
The OSI layers, also known as the Open System Interconnection layers, play a vital role in computer security and communication across networks. Published by the International Organization for Standardization (ISO) in 1980, the OSI Model is a conceptual framework that efficiently manages computing functions and facilitates global data transmission through its seven distinct layers. The Physical Layer concerns with the physical medium, including the electrical, mechanical, and functional aspects of the network. This layer is responsible for transmitting raw binary data across physical media such as cables, wireless links, and optical fibers, ensuring accurate and reliable data exchange between devices.
The Physical Layer is highly susceptible to security vulnerabilities such as rogue devices, that can evade detection without adequate protection. These hardware attack tools can lead to substantial damage within enterprise networks, compromising sensitive data and disrupting operations. Additionally, spoofed peripherals can impersonate legitimate Human Interface Devices (HIDs), amplifying the risk to network integrity. This makes Layer 1 security an essential consideration for any robust cybersecurity strategy.
Physical Layer Security
Sepio’s patented technology delivers unmatched visibility and control at the Physical Layer, offering comprehensive protection against threats that evade traditional traffic-based security solutions. Our cutting-edge Asset Risk Management (ARM) solution proactively identifies hidden risks and mitigates potential attacks targeting Layer 1 security, ensuring robust hardware security and maintaining the integrity of your network.
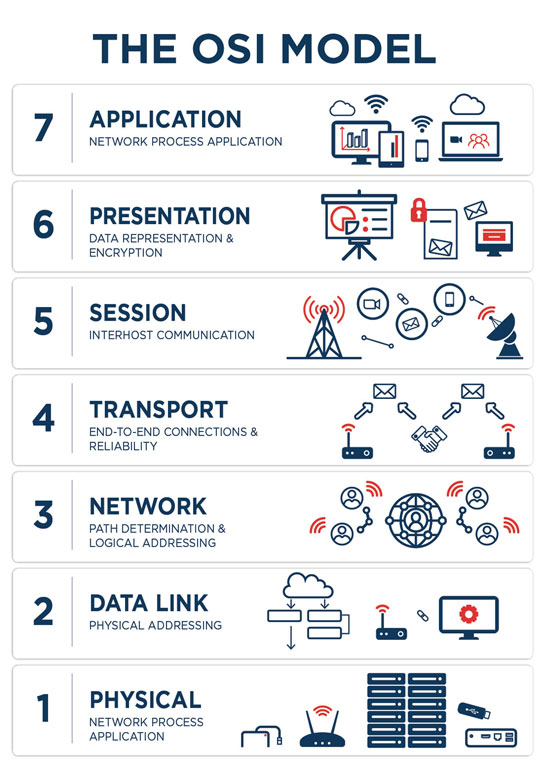
Why Layer 1 Data Matters?
Traditional network security solutions, such as Network Access Control (NAC), Intrusion Detection Systems (IDS), and IoT security scanners, often fall short when it comes to detecting threats at Layer one. Devices like unmanaged switches, passive taps, and out-of-band equipment can easily bypass traffic-based systems, remaining undetected. Even more concerning, spoofed devices can impersonate legitimate hardware, effectively circumventing existing security measures. Achieving complete visibility into the Physical Layer is essential for securing your network.
Without this level of insight, you cannot fully safeguard your network infrastructure from cybercriminals and sophisticated, malicious attacks.
The Risks of Ignoring Physical Layer Visibility
Cybercriminals and state-sponsored hackers are well aware of the vulnerabilities in the Physical Layer and actively exploit the gaps in network security. By leveraging passive implants or device spoofing, they can gain unauthorized access to critical systems without detection. For instance, a seemingly innocent Raspberry Pi could be used to impersonate a legitimate device, resulting in severe security breaches.
IoT devices, with their use of MAB (MAC Authentication Bypass), are your ‘soft underbelly.’ Implementing 802.1x but then setting up exceptions for non-802.1x-compliant devices (e.g., IP cameras, printers) creates a significant security gap. Hackers are skilled at targeting these gaps and using them to infiltrate your network. To counteract this, it’s critical to apply layer 1 security principles and gain total visibility over physical layer devices.
Physical Layer in Network Security
The Physical Layer, denoted as layer 1 in the OSI model, serves as the foundational tier responsible for overseeing hardware security. The physical layer concerns with establishing and manage the physical connections between devices, identifying the equipment engaged in data transmission. Layer 1 encompasses the definition of hardware components, cabling, wiring, as well as the management of frequencies and pulses. Information is transmitted in the form of bits, with nodes facilitating its transfer from one point to another.
However, a pressing concern lies in the neglect of hardware security within this layer. Current security software solutions fail to encompass the Physical Layer (Layer 1) of the OSI model. As a result, security teams lack visibility into the physical infrastructure of the network, making it easier for rogue devices to go undetected, leading to potential data security breaches.
Without proper visibility into the Physical Layer, enterprises are at heightened risk of rogue devices infiltrating their networks and executing harmful, hardware-based attacks. Since Layer 1 is the starting point for data transmission, it is essential to implement strong security measures at this foundational level to prevent attacks before they can spread through the network. Establishing robust Layer 1 security is crucial for protecting an organization’s infrastructure from the potentially devastating effects of rogue device attacks.

Endpoint and Network Security
Sepio’s Asset Risk Management (ARM) provides unmatched visibility at the Physical Layer, going deeper than traditional traffic-based solutions. Unlike solutions that rely on device traffic to detect threats, ARM uses Layer 1 data to validate devices and connections, enabling a true trust and verify approach.
With Sepio’s solution, you can:
- See all network assets, both known and hidden.
- Prioritize vulnerabilities and mitigate risks effectively.
- Gain better control over asset risks with an advanced, hardware-focused security approach.
Speak with an Expert Today
Learn how Sepio’s patented technology can transform your information security by providing the necessary Physical Layer visibility to detect and prevent sophisticated attacks. Speak with an expert today to enhance your hardware security strategy and protect your enterprise from security breaches and compromised systems.
Read the Physical Layer Visibility brief (pdf)