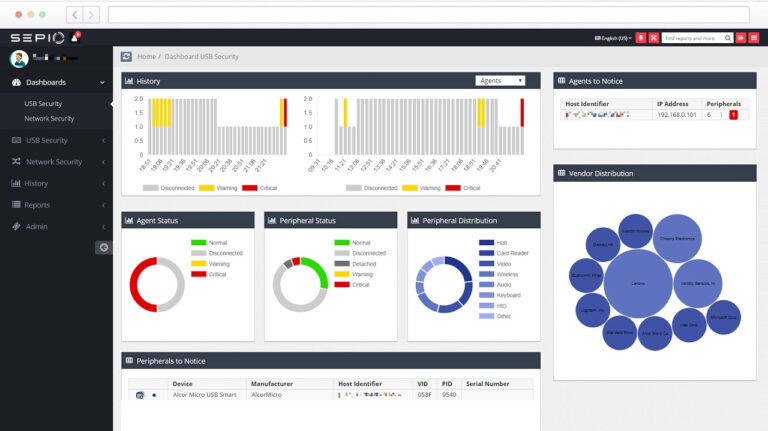
Risk insights and vulnerable peripherals are crucial elements in modern cybersecurity strategies. Risk insights involve the continuous evaluation and analysis of potential threats, helping organizations understand and manage vulnerabilities in their systems. This includes identifying, assessing, and prioritizing risks to ensure data confidentiality, integrity, and availability, and to protect against threats that can impact the organization’s overall security posture.
Vulnerable peripherals, such as USB devices, printers, cameras, external hard drives, and other connected devices, are often overlooked entry points for cybercriminals. These peripherals, when compromised, provide attackers with opportunities to bypass traditional security defenses. Devices like rogue USB drives or unsecured external storage units can deliver malware, intercept sensitive data, or provide backdoor access to otherwise secure systems. With the increasing adoption of IoT devices, the attack surface is expanding, making it critical for organizations to implement robust security measures for peripheral protection.
The Importance of Physical Layer Visibility in Managing Vulnerable Peripherals
To mitigate the risks associated with vulnerable peripherals, organizations need enhanced visibility and control over their physical network layer. Sepio’s platform provides advanced, patented technology designed to secure this foundational layer of network infrastructure. By offering deep visibility into every connected device, Sepio helps organizations identify and assess risks associated with vulnerable peripherals in real-time, ensuring that no malicious or unauthorized device goes undetected.
Sepio’s Asset DNA technology goes beyond traditional methods by focusing on the physical attributes of each device rather than just its behavior. This allows for precise categorization of devices, whether they are managed, unmanaged, or deliberately hidden. By continuously monitoring the presence of devices, Sepio offers a comprehensive view of all peripherals, from IoT devices to legacy hardware.
With the ability to prioritize assets based on their risk level, Sepio helps organizations enforce strict hardware access controls. The platform autonomously blocks rogue devices or peripherals that violate predefined rules, ensuring only trusted, authorized devices can interact with the network. This proactive approach not only secures vulnerable peripherals but also strengthens the overall security framework by addressing threats at the physical layer, where many attacks often begin.