Cyber insurance, also known as cybersecurity insurance or cyber risk insurance, is a type of insurance coverage designed to protect businesses and individuals from financial losses and liabilities associated with cyber threats and incidents. These threats can include data breaches, hardware attacks, ransomware attacks, denial of service attacks, and other forms of cybercrime.
CyberSecurity Insurance Risk Framework
As the threat landscape evolves, cybersecurity insurance has become essential for mitigating cyber risk. One notable development in this field is the New York Cyber Insurance Risk Framework (CIRF). This framework, introduced by the New York Department of Financial Services (NYDFS), provides a structured approach to help businesses navigate cyber risks, including non-affirmative cyber risk, and manage their insurance strategies. It emphasizes the need for insurers to price cyber risks appropriately and offers financial incentives to improve security measures, potentially lowering premiums for organizations that enhance their cybersecurity posture.
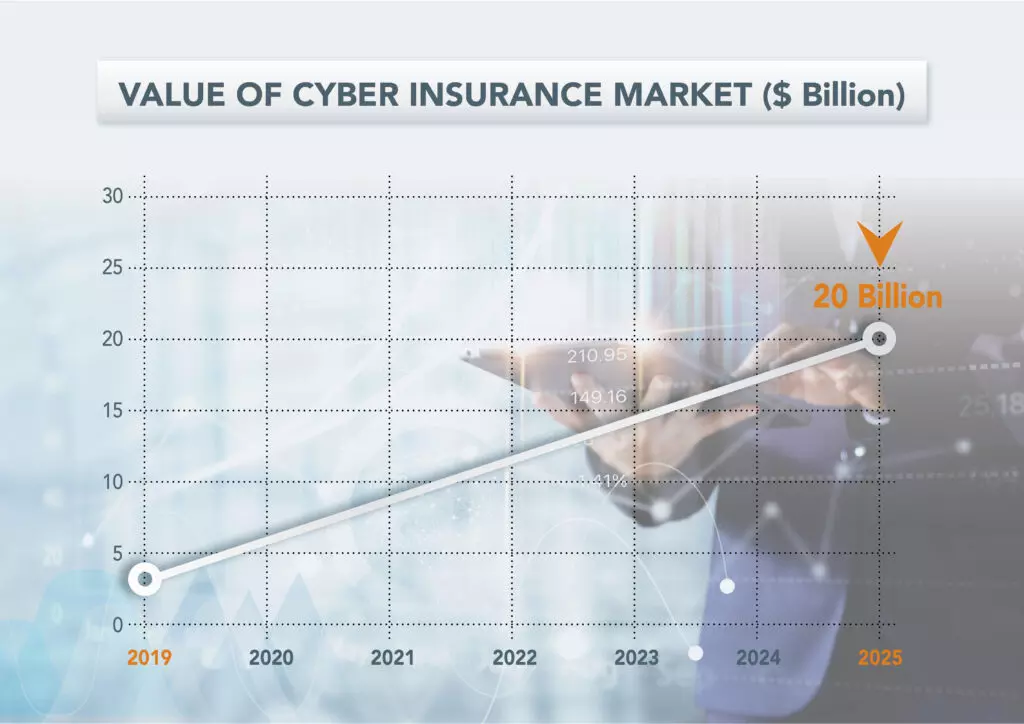
The framework was a response to the rise in cyberattacks, exemplified by incidents like the SolarWinds attack, where a Russian-affiliated hacking group infiltrated the systems of multiple U.S. government agencies, including the US Treasury and the Department of Commerce. With cybersecurity becoming increasingly crucial, the cyber insurance market is projected to grow from $3.15 billion in 2019 to $20 billion by 2025.
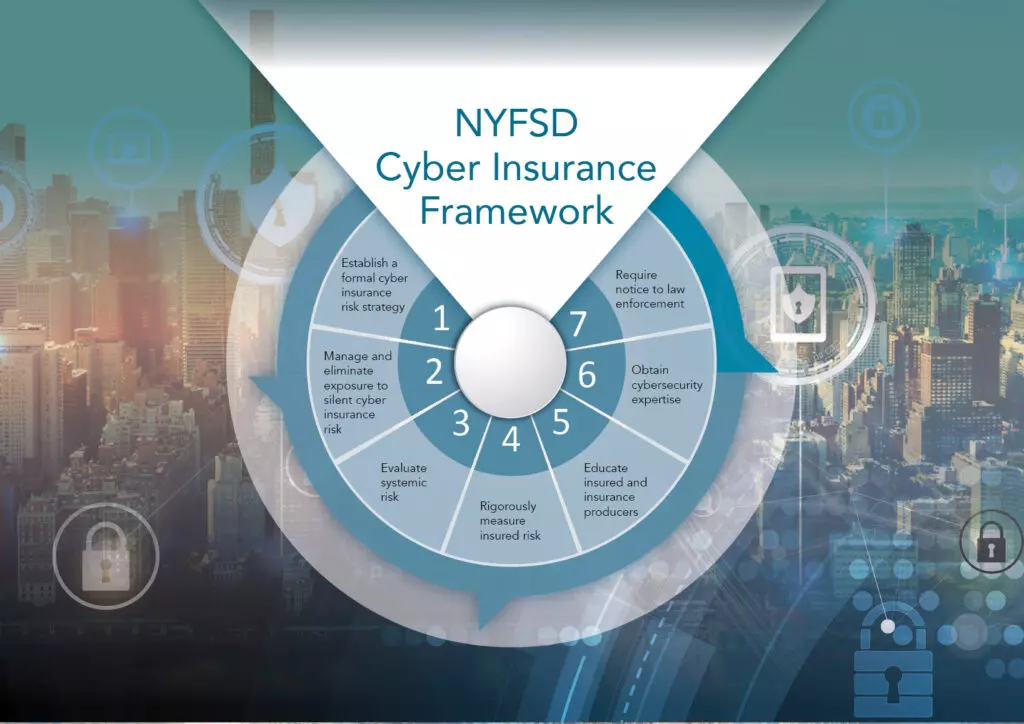
Establish a Formal CyberSecurity Insurance Risk Strategy
For insurers to effectively measure cyber insurance risk, including non-affirmative cyber risks, both qualitative and quantitative strategies are necessary. These strategies should be directed and approved by senior management and the board. A strong strategy should include the following components:
- Manage and Eliminate Exposure to Non-Affirmative Cyber Risk: Insurance carriers need to identify and evaluate their exposure to silent, or non-affirmative cyber risk, under non-cyber policies. Subsequently, they should reduce such exposure. Insurers can eliminate cyber risks by making clear, in any policy that could be subject to a cyber-related claim, whether the policy provides or excludes coverage for cyber-related losses.
- Evaluate Systemic Risk: Systemic risks, like those caused by third-party vendors, can result in simultaneous losses for multiple insured parties. Insurers must conduct stress tests and model catastrophic cyber events. The SolarWinds attack is an example of a systemic risk that could damage many insureds simultaneously.
- Rigorously Measure Insured Risk: Insurers must develop a data-driven plan to assess the cyber risks of each insured. This includes evaluating governance, vulnerability management, access controls, incident response, and third-party risk management.
- Educate Insured Parties and Insurance Producers: Insurers should educate policyholders and brokers about the importance of robust data privacy and security programs. Incentives, such as policy pricing and access to cybersecurity services, can drive improvements.
- Obtain Cyber Expertise: In order to evaluate cyber risks, insurers must have the appropriate level of expertise. Hence, this requires the recruitment of employees with cyber experience and skills. Moreover, insurers should commit to training and developing personnel.
- Require Notice to Law Enforcement: Cybersecurity insurance policies should mandate that policyholders report attacks to law enforcement, which can aid in recovering stolen data and deterring future crimes.
The Growing Importance of CyberSecurity Insurance
As cyberattacks grow in frequency and sophistication, the importance of cyber insurance becomes more pronounced. The New York Cyber Insurance Risk Framework sets a new standard for insurers to address the rapidly evolving cyber threat landscape.
Hardware attacks are extremely challenging to mitigate due to their extremely covert nature. Network Implants can evade existing cyber software solutions by sitting on the physical layer, and Spoofed Peripherals impersonate legitimate HIDs and are therefore not detected as harmful. With this, cyber insurance is a necessary tool, and a framework will provide a coherent resource for insurers to refer to when creating their policies.
While New York may be the first state to introduce such a framework, it is unlikely to be the last. This could mark the beginning of a global push to establish cyber insurance risk frameworks that offer clear guidelines for insurers worldwide.
Sepio’s Endpoint and Network CyberSecurity
Protect your organization with Sepio’s comprehensive asset visibility and real-time risk management. Detect and mitigate threats from malicious hardware devices across your network, including those connected via USB and network interfaces. With Sepio, you’ll have:
- Complete visibility of all connected assets, ensuring no device goes undetected.
- Hardware-based risk assessments to identify vulnerabilities and threats in real-time.
- Immediate blocking and control of risky assets, preventing security breaches before they happen.
- Customizable policies to manage USB and network interfaces effortlessly.
Secure your infrastructure with the most advanced endpoint and network cyber security solution. Schedule a demo and see how Sepio can safeguard your assets!






