What is a Supply Chain Cyber Attack?
A supply chain cyber attack is a type of cybersecurity threat where malicious actors exploit vulnerabilities in an organization’s extended network of suppliers, vendors, and service providers. Instead of targeting the organization directly, attackers infiltrate less secure third-party entities, such as software suppliers, contractors, or cloud service providers, and use these trusted connections as entry points to bypass security defenses.
Supply chain cyber attacks highlight the growing importance of supply chain cybersecurity, as the interconnected nature of modern business ecosystems means a single compromise can ripple across multiple organizations. This makes third-party risks one of the most critical challenges facing enterprises today.
Supply Chain Cybersecurity
Effective supply chain cybersecurity requires securing every stage of the supply chain against potential threats. This includes implementing controls to manage risks from third-party entities such as contractors, vendors, and software providers (NIST SP 800-161). The goal is to ensure that trust in suppliers does not become a hidden weakness.
Organizations can reduce their exposure to cyber supply chain cyber attacks by adopting strategies such as Zero Trust Architecture (ZTA), ongoing monitoring of third-party access, and rigorous vendor risk assessments. By proactively addressing these risks, businesses strengthen their resilience against one of the most challenging cyber attack vectors in today’s cybersecurity landscape.
Why Supply Chain Cybersecurity Matters
Supply chains are the backbone of modern business, but they also represent one of its weakest links. A single vulnerability in a vendor, contractor, or software supplier can quickly cascade into a large-scale security incident. According to the U.S. Government Accountability Office (GAO-18-667T), reliance on supply chains introduces risks at every stage of an information system’s lifecycle, creating opportunities for attackers to infiltrate critical environments.
The impact of supply chain cyber attacks extends far beyond technical disruption. Hackers can cause widespread outages, steal sensitive data, or even gain long-term control over critical systems. Social engineering tactics and sourcing from unverified suppliers only amplify these risks, leaving organizations exposed to credential theft, compliance violations, and reputational damage.
As supply chains become more digital and globally interconnected, organizations often lack full visibility into their extended network of vendors. This lack of transparency makes it difficult to identify hidden risks. With increasing reliance on cloud services, IoT devices, and outsourced operations, the cyber attack surface continues to expand, making supply chain cybersecurity an essential focus for every organization in 2025.
Examples of Supply Chain Cyber Attacks
One of the most significant examples of a supply chain cyber attack is the SolarWinds incident of 2020. In this case, attackers compromised SolarWinds’ Orion software updates and inserted malicious code, known as SUNBURST. When customers downloaded routine updates, they unknowingly installed the backdoor, giving attackers long-term access to their networks.
This supply chain cyber attack affected thousands of organizations worldwide, including U.S. federal agencies and major enterprises. It demonstrated how a single compromised vendor can create widespread vulnerabilities across an entire ecosystem.
The SolarWinds incident underscored the urgent need for stronger supply chain cybersecurity practices. Continuous monitoring, thorough vendor risk assessments, and adopting a Zero Trust (ZTA) approach are now essential strategies to reduce exposure to similar large-scale supply chain cyber attacks.
Key Vulnerabilities in the Supply Chain
Complex and Interconnected Supply Chains: A large supply chain makes it harder to detect and trace attacks. Moreover, the involvement of many suppliers and subcontractors complicates investigations. Consequently, hackers benefit from multiple entry points, where even one weak supplier can compromise the entire network.
Additionally, insider threats, both careless and malicious, are amplified as more individuals gain access to the supply chain. Lack of training often leads to unintentional risks, while malicious insiders may exploit opportunities for personal gain or revenge.
Risks from Foreign Suppliers: Working with suppliers overseas introduces geopolitical risks. Attackers may exploit international relationships to launch cyberwarfare supply chain attacks. Countries with weak cybersecurity regulations create easier targets for attackers, who can then pivot into organizations in more secure regions.
Insufficient Supplier Cybersecurity Measures: Even in regulated industries, many suppliers struggle with limited budgets or outdated tools. Since an organization is only as strong as its weakest link, poorly protected suppliers can expose the entire supply chain to cyber attacks.
Types of Supply Chain Cyber Attacks
Supply chain cyber attacks can target software, hardware, or firmware, and adversaries often exploit multiple vectors simultaneously. These attacks are particularly dangerous because they can remain invisible while causing data theft, espionage, or long-term control of critical systems.
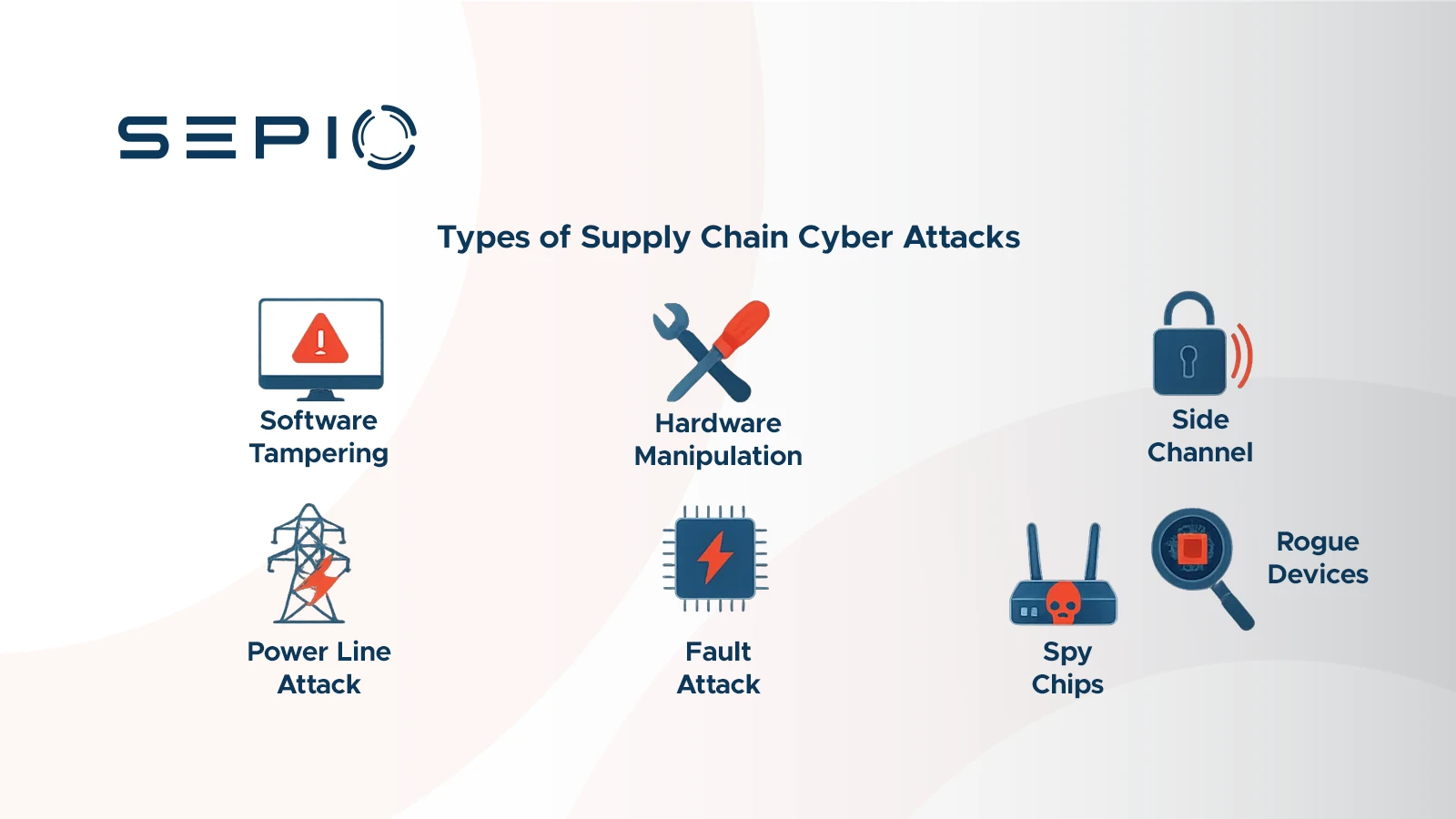
Software Tampering
Attackers compromise software updates or applications used by organizations, inserting malicious code that is distributed to all customers who install the updates. Examples include attacks on IT management software or widely used utilities (CISA, 2021).
Hardware Manipulation
Malicious actors can modify hardware components, such as chips or printed circuit boards (PCB). Even though the device retains its normal function, hidden capabilities can be triggered remotely or through physical signals, creating covert attack pathways.
Manipulation can happen at any point in the device’s supply chain. Someone may open the device, change its components, close it, and send it back into transit.
Side Channel Attacks
These attacks extract secrets from a system by analyzing physical characteristics such as timing, power consumption, electromagnetic emissions, or even sound. Techniques include acoustic cryptanalysis, thermal imaging, and power analysis to reveal encryption keys or sensitive information.
Fault Attacks
Hackers apply abnormal voltage, temperature, or signals to electronic devices. This stress causes errors that can expose sensitive outputs or cryptographic keys.
Power Line Attacks
Hackers can use malware to control a device’s Central Processing Unit (CPU) workload. This allows them to manipulate power consumption patterns and steal passwords, encryption keys, or other sensitive data.
Wireless Implants and Rogue Devices
Attackers exploit device acceptance protocols like HID (keyboards, mice) to introduce malicious peripherals. These devices appear genuine to the system and user but allow remote control of the endpoint.
Spy Chips
Tiny harmful chips embedded in hardware can access firewall configurations, modify settings, or monitor network activity. Activation may be time-delayed or started by specific conditions, making them nearly impossible to detect using conventional methods.
How to Prevent Supply Chain Cyber Attack
Preventing cyber supply chain cyber attacks requires a combination of physical inspections, advanced testing, and continuous monitoring. Key strategies include:
Automated Optical Inspection (AOI): Originally used on assembly lines, AOI quickly inspects populated PCBs against a “golden image” to detect component modifications or soldering inconsistencies. While highly accurate, AOI requires direct visual access to the PCB, which can be challenging once devices are deployed.
JTAG Boundary Scan: This technique tests interconnects on PCBs or within integrated circuits. It can be used during development, production, and in-field testing, providing detailed information about a board’s state. However, direct internal access is required, making post-deployment checks more difficult.
Radio Frequency (RF) Power Detection: Monitoring RF emissions can help detect hidden signals from compromised devices. Attackers may attempt to conceal these signals using unfamiliar RF bands or spread-spectrum techniques, so continuous monitoring is essential.
Power Line Anomaly Detection: Data exfiltration can occur over standard power cabling. Analyzing physical-layer characteristics of power lines can detect digital data “piggy-backing” on these channels.
X-ray Inspection: X-ray scans allow detection of additional or modified modules without opening a device, which is useful for keeping warranties valid. By comparing scans to golden images or databases of similar devices, hidden modifications can be identified.
Physical Layer Fingerprinting: By analyzing voltages, currents, signal patterns, and PoE parameters, each device can be assigned a unique physical fingerprint. AI or ML algorithms can then detect anomalies, as used in Sepio platform.
Using these methods along with strong monitoring and risk management helps organizations defend against supply chain cyber attacks. It also strengthens overall supply chain cybersecurity.
The Sepio Solution for Supply Chain Cyber Attacks
Sepio’s Asset Risk Management platform provides complete visibility into all known and shadow assets across your environment. By creating a unique DNA profile for every asset, Sepio eliminates false assumptions and uncovers hidden risks that could lead to supply chain cyber attacks.

Sepio assigns an Asset Risk Factor (ARF) score to every asset based on its DNA, behavior, and context. The system immediately flags high-risk assets, such as those that could lead to supply chain cyber attacks. Continuous monitoring tracks changes in real time, while machine learning and threat intelligence help improve IT efficiency.
Sepio automatically enforces detailed access rules. As soon as an asset breaks a rule or connects to a known threat, Sepio blocks it. Consequently, this reduces the risk of a compromised supply chain.
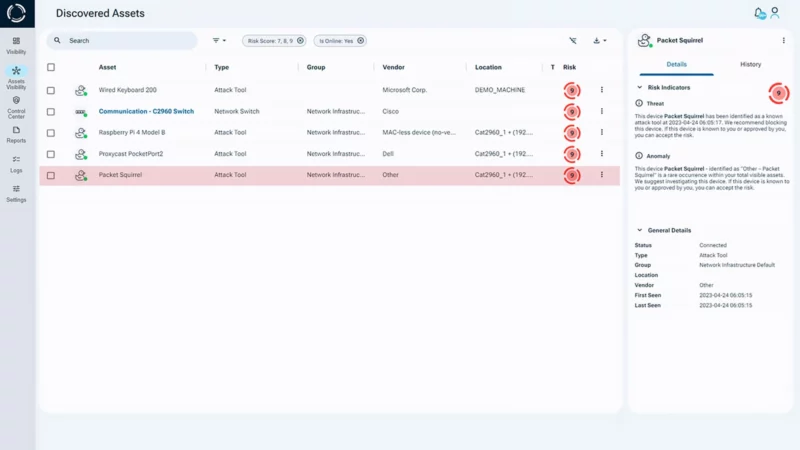
Sepio can be deployed quickly and scales across your entire environment in under 24 hours. As a result, it avoids IT disruption, prevents privacy issues, and eliminates compliance risks.
Sepio enhances the value of existing cybersecurity solutions like NACs, EDRs, XDRs, and Zero Trust platforms by adding visibility and context they can’t achieve alone. As a result, your organization is better equipped to defend against supply chain cyber attacks and other critical threats.
Take Control of Your Supply Chain Security
Prioritize and reduce risks related to supply chain cyber attacks. Schedule a demo to understand how to use Sepio’s patented technology to gain control of your asset risks.
Read the Supply Chain Cyber Security E-Book (pdf)





