Network Security Visibility
In today’s rapidly evolving cyber threat landscape, network security visibility is more crucial than ever. Organizations must have accurate, real-time insight into every network-connected and peripheral device to detect, monitor, and prevent hardware-based threats and vulnerabilities. Without this visibility, companies risk leaving critical devices and endpoints invisible to traditional security tools, creating hidden entry points for attackers.
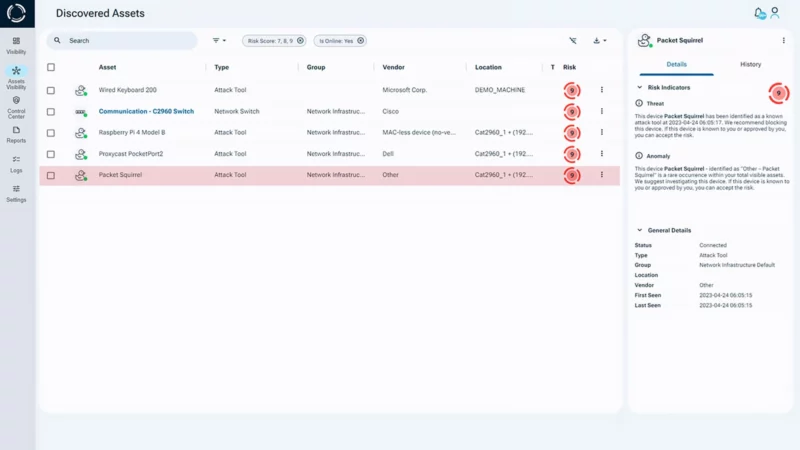
However, most conventional tools cannot identify devices lacking a digital footprint, leaving organizations exposed to shadow IT, rogue devices, and undetected hardware risks. That’s where Sepio’s Asset Risk Management (ARM) solution comes in. ARM bridges the visibility gap by delivering unparalleled network security visibility across IT, OT, and IoT environments, helping organizations protect both their digital and physical infrastructure.
Reveal Hidden Devices. Achieve Network Security Visibility
Sepio’s ARM solution revolutionizes hardware security by uncovering hidden threats across network and peripheral interfaces, including USB, Bluetooth, and other connected devices. By collecting Physical Layer data from switches and endpoints, ARM delivers continuous, real-time visibility of all network and peripheral assets, without requiring additional hardware deployments. This level of network visibility for cybersecurity ensures that no device goes unnoticed, even those intentionally or accidentally hidden from traditional tools.

With deep hardware intelligence, policy-based control, and automated risk mitigation, ARM empowers organizations to take back control of their hardware landscape.
Detect Hidden Network and Peripheral Threats Effectively
Organizations today face significant challenges in tracking every hardware asset, particularly across mixed IT, OT, and IoT environments. Many security teams are unaware of hidden endpoints or peripheral devices that can serve as entry points for malicious activity. Achieving network security visibility is critical for defending against both external attacks and internal threats, including insider misuse or negligent device usage.
Sepio addresses these challenges by delivering comprehensive network visibility and control, regardless of device type, manufacturer, or interface. With real-time monitoring of all connected hardware and peripheral devices, organizations can ensure that critical assets are always visible, continuously monitored, and fully protected. This enhanced network security visibility allows security teams to quickly identify hidden risks, prioritize mitigation efforts, and maintain regulatory compliance across IT, OT, and IoT networks. For further guidance on network security hardening and improving visibility, organizations can refer to CISA’s official recommendations.
Benefits of Sepio Asset Risk Management
Implementing Sepio’s ARM solution for network and peripheral asset visibility provides organizations with numerous benefits for strengthening hardware security and enhancing overall cybersecurity posture.
Complete Visibility of All Hardware Assets: ARM delivers full visibility into every connected device, including endpoint peripherals and devices across IT, OT, and IoT networks. By leveraging physical layer fingerprinting and data augmentation from endpoints and network infrastructure, Sepio ensures that both known and shadow devices are detected, enhancing network security visibility and reducing the risk of hidden threats
Full Control with Predefined Policies: ARM allows organizations to enforce enterprise-wide policies that comply with regulatory standards and best practices. With predefined policy templates and no need for baselining, ARM simplifies deployment while seamlessly integrating into existing security ecosystems. This ensures consistent security across all network devices, increasing visibility and control over the organization’s hardware landscape.
Rogue Device Mitigation (RDM): ARM automatically identifies and mitigates threats the moment rogue or suspicious devices are detected. Integration with Network Access Control (NAC) and Security Orchestration, Automation, and Response (SOAR) platforms enhances response capabilities, enabling organizations to rapidly neutralize risks while maintaining continuous network security visibility.
Enhanced Threat Detection Across IT, OT, and IoT: By providing end-to-end visibility across all network segments, ARM ensures that cybersecurity teams can monitor, detect, and respond to potential threats in real time. This is particularly critical in industrial OT environments, where unmonitored devices can disrupt operations or create vulnerabilities that bypass traditional IT security measures.
See Every Known and Shadow Asset. Prioritize and Mitigate Risk
Network security visibility is no longer optional. It’s essential for organizations aiming to secure every connected device. Sepio’s ARM solution allows organizations to see and control every device on the network, prioritize risks based on severity, and mitigate threats before they can cause damage.
Speak with one of our experts to learn how Sepio’s patented technology provides unmatched hardware security, ensuring complete visibility, control, and risk mitigation across IT, OT, and IoT networks. By implementing ARM, organizations can achieve continuous network security visibility, reduce hidden risks, and maintain regulatory compliance with ease.
Download Case Study





