A network backdoor refers to a secret or unauthorized method of accessing a computer network, usually for malicious purposes. It’s essentially a hidden entry point into a network that bypasses normal security controls, allowing an attacker to gain unauthorized access, control, or manipulate network resources.
Network backdoors pose a significant cybersecurity risk to organizations. They are often difficult to detect and can lead to data breaches, financial losses, and reputational damage. Preventing and mitigating network backdoor threats requires a combination of strong security practices, employee training, and advanced cybersecurity technologies like asset risk management solutions.
Zero Day Vulnerabilities
In today’s hyper-vigilant cybersecurity landscape, zero-day vulnerabilities and emerging attack methods capture attention. However, even seemingly traditional threats—such as a network backdoor—can still pose significant risks.
Discovering the Network Backdoor
During a deployment of Sepio’s platform for a multi-campus organization, we discovered a network backdoor that had gone unnoticed for months. The former network manager had left the organization, and during our visibility scans, we detected an unauthorized device embedded within the infrastructure.
A Raspberry Pi Connected to a Switch
We assisted the organization’s IT team in setting up network polling tools to gain full visibility. During this process, we identified an Raspberry Pi connected to a switch on another campus, thousands of miles away (Raspberry Pi Security). This was a cause for concern, because the IT staff was unaware of this device or its purpose. As such, they had someone on the respective campus go down to the network room in question and take a photograph.

And this is where things became interesting. The Raspberry Pi was connected to a USRobotics modem which was connected to a phone line. In addition, the Raspberry Pi was also connected to a USB RS-232 Serial Adapter which was connected into the console port on the network switch. A backdoor into the network had been discovered.
Tracing the Network Backdoor to a Forgotten Machine
To understand what had transpired, we did a search after deploying the Sepio Agent onto all of the IT office computers. On one particular Linux machine, we found another modem. This computer, of course, had been used by the former network manager, and no one had touched it since their departure. Given my curious nature, I asked if anyone could log into the system. The network manager had documented many things, although unfortunately not this backdoor, but had left credentials for the machine. A young helpdesk technician was able to login using the credentials, as other technicians watched.
Remote Connectivity
Finding nothing notable in the applications, one of the other technicians mentioned that the former network manager had used terminals a lot. Scrolling through the applications again, we came across Terminator, and the delighted helpdesk tech eagerly launched the application and then sat stumped at the prompt. I told him to try minicom, and the program opened as soon as the tech pressed ENTER. After a couple of attempts at getting the CTRL-A then Z combination right, the menu appeared, and I asked the tech to press “D.” A single number appeared in the dialing directory. I asked if we could attempt the connection. Much to my delight, the request was granted by the manager. The helpdesk tech selected the number and pressed ENTER. A dial-tone came to life and numbers began dialing. . .
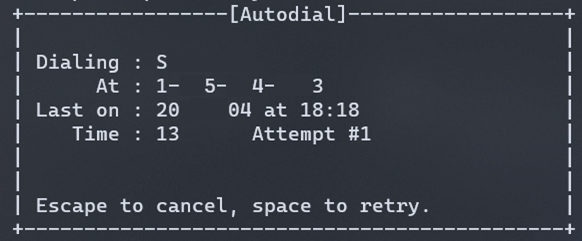
Shortly after, the screech of data scratching its way through the phone lines filled our ears! The helpdesk tech asked, “What’s that?” Everyone else laughed, having at least grown up knowing those sounds intimately. I smiled and told him to search for modem sounds later. And, then they stopped.
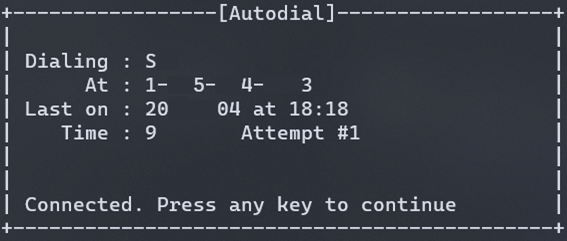
Connected. Connected! We had a connection! Pressing any key, we were greeted with our spoils! The helpdesk tech logged into the Raspberry Pi with another set of credentials!
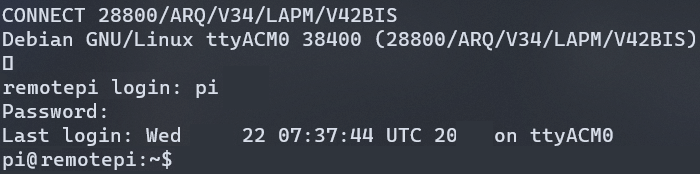
It didn’t take long, but we found our way into the switch.
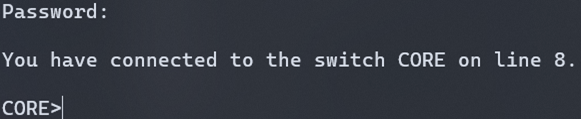
Remote Access to the Forgotten Network
From thousands of miles away, we had dialed a phone number and been connected to a remote network using a modem. One of the other technicians recalled that the Internet connection on that particular campus was problematic at times. The former network manager had installed the Raspberry Pi and modem as a backup. We had opened that door and walked through; a door that had been hidden until uncovered by the network visibility provided by Sepio.
This situation underscores the importance of continuous asset visibility and risk management. Without Sepio’s platform, this network backdoor could have remained undiscovered, leaving the organization vulnerable to unauthorized access and cyber threats.
Eliminate Hidden Network Backdoors with Sepio
Network backdoors are an invisible risk that can compromise even the most secure environments. Sepio provides comprehensive hardware asset risk management to uncover hidden threats, ensuring your organization remains protected.
Schedule a Demo today and discover how Sepio can enhance your network security and eliminate hidden threats.






