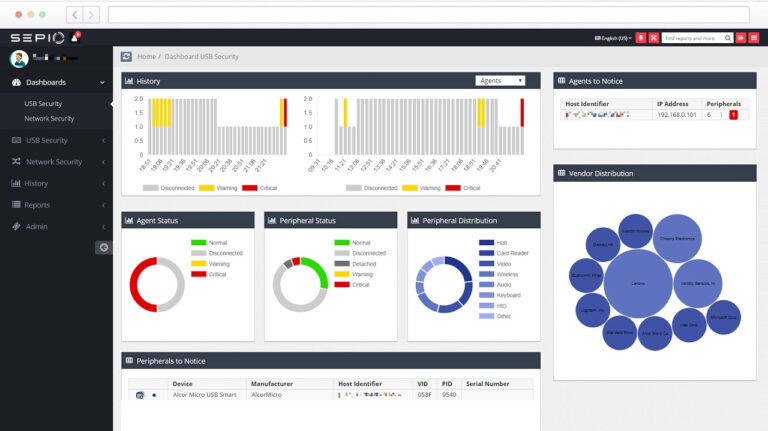
Sepio Lab Demo Tools video includes Sepio’s HAC-1 benefits, such as gaining full visibility into all assets, detecting rogue devices, and more.

Home / Resources /Sepio-academy
Sepio Lab Demo Tools video includes Sepio’s HAC-1 benefits, such as gaining full visibility into all assets, detecting rogue devices, and more.

Global Event: Industrial Cyber Security, IIoT & IoMT
Sepio Academy – Zero Trust Hardware Access
Related Posts

Subscribe to Sepio Newsletter
Get the recent updates from Sepio directly in your inbox.
Subscribe NowRecent Posts

ThinkShield Hardware Defense Partnership May, 2025

Realcomm 2025. The New ROI: Return on Innovation February, 2025

Infosecurity 2025. Building a Safer Cyber World February, 2025
Tags